Anatomy of 2,000 Compromised Web Servers used in DDoS Attack
One of our clients was being attacked by a layer-7 DDoS attack for more than a week. The attack was generating around 5,000 HTTP requests per second, which took his site and server down. It also caused his hosting company to suspend his server for “ToS violation”. Yes, some hosting companies consider a ToS violation if you are suffering a DDoS. It is mostly an excuse to protect their networks, but very annoying for someone victim of an attack.
After a week of pain, he found our Website Firewall (WAF) product, the rest as they say is history. We were able to quickly block the attack and restore his site to normal operations. If that was all that there was to the story, then many would find this to be a very uninteresting story.
A Diamond in the Ruff
As is customary in our lab, we began analyzing the attack to see if there was anything else we could learn. That is when we noticed something curious, the IP addresses hitting the server were always constant.
We did some operating system identification (using p0f) and the attack was coming mostly from web servers running on Windows and Linux:
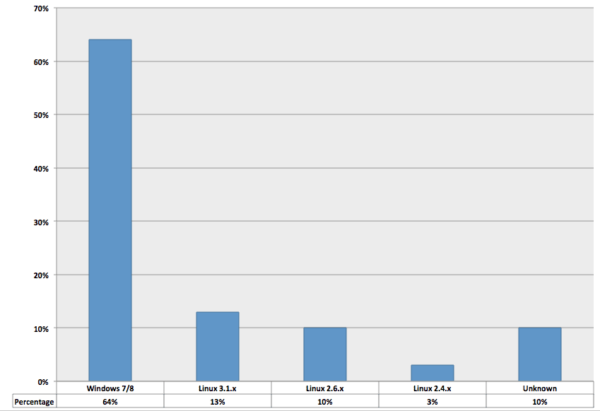
This is a bit unusual, most layer-7 DDoS attacks leverage compromised desktops and very few of them actually run on Linux. We also started checking the banners of these IPs and we saw a variety of web servers, but the majority of them were running Apache:
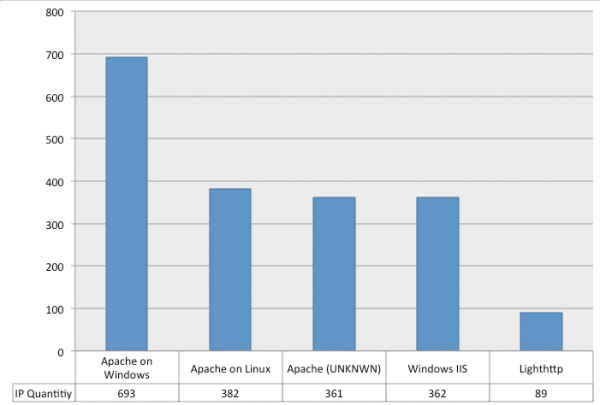
There were also a number of other IP addresses that were not displaying the server banner (or too slow to respond to our HTTP queries). This is the breakdown of the most used web servers on the IP addresses attacking our client:
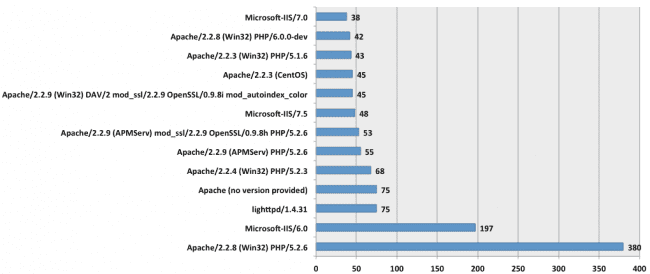
These were but a subset of the most active, in total we found close to 2,000 different IP addresses causing the damage (each one hitting the server a few times per second).
As far as location, most of them were coming from China, Taiwan and Thailand:
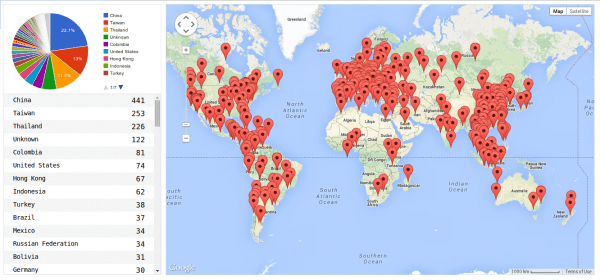
Another interesting point is that more than 300 of them were using “AppServ Open Project” (version 2.5.9 or 2.5.10), which unfortunately bundles an old and outdated version of PHPMyAdmin.
Compromised Web Servers
From what we could gather, it seems someone created a bot net of compromised web servers that are running AppServ, outdated Apache, outdated IIS and other vulnerable software (e.g., PHPMyadmin).
This setup gives the attackers good power when attacking sites as they remain anonymous behind proxies. In this scenarios, they specifically focused on Layer 7 HTTP flood attacks, but it could have as easily been DNS application, an SSDP attack or any number of the available options when it comes to DDoS.
We will be contacting the network/hosts responsible for them to see if we can get them patched or shut down.
If your are a victim of a DDoS attack and need help, let us know, we’d love to help, you can start here.



No comments yet.