Critical Vulnerability in Joomla! HD FLV Player Plugin
We’ve been notified of a critical vulnerability affecting the HD FLV Player plugin for Joomla!, WordPress and custom websites. It was silently patched only Joomla! and WordPress, leaving the custom website version vulnerable.
Furthermore, websites running this plugin are also at risk of being abused to send spam emails, an issue which wasn’t fixed in the updated version.
Impacts of the Vulnerability
Websites using one of the aforementioned CMS applications and running an outdated version are vulnerable to an Arbitrary File Download vulnerability which could be used, depending on the platform, to take control of the targeted website. The websites using the custom version of this plugin are still vulnerable to this vulnerability.
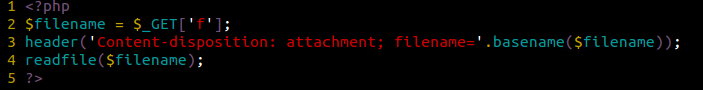
The issue is found in the following files: download.php and email.php
This is what the Download.php code looks like:
From this snippet we can see how the attacker is able to upload almost any file they like to the server. There are no security checks being applied before accessing this file, making it accessible, and exploitable, to anyone that knows the url structure to the file.
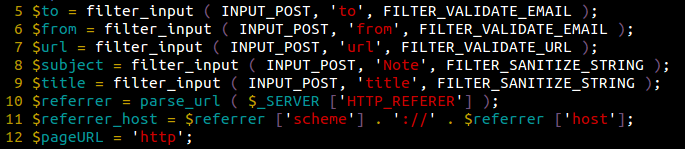
Same thing goes for email.php, it filters the variables used to send emails:
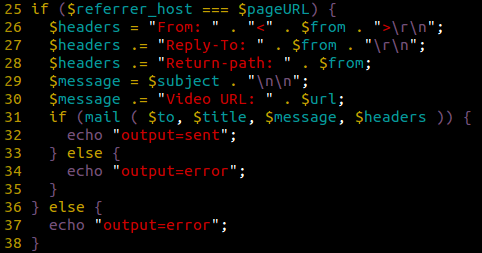
Then it assumes that if the provided “Referrer” field fits the website’s URL, then it’s okay to send this email:
Unfortunately, the “Referer” field can easily be modified by the attacker to match pretty much anything they want, so it’s not any more secure to validate requests this way.
Update (or delete)!
This is a critical vulnerability.
If you use this plugin on a custom website, we highly recommend you to either remove these two files (download.php and email.php). For WordPress/Joomla! users, be sure to update your plugins/extensions; in this instance applying an update should protect you from the Arbitrary File Download vulnerability. You should still remove the “email.php” file from your site to prevent your mail server’s IP from getting blacklisted, something we see often.



No comments yet.