Introducing TLS 1.3
CloudFlare is turbocharging the encrypted internet
The encrypted Internet is about to become a whole lot snappier. When it comes to browsing, we’ve been driving around in a beat-up car from the 90s for a while. Little does anyone know, we’re all about to trade in our station wagons for a smoking new sports car. The reason for this speed boost is TLS 1.3, a new encryption protocol that improves both speed and security for Internet users everywhere. As of today, TLS 1.3 is available to all CloudFlare customers.
The Encrypted Internet
Many of the major web properties you visit are encrypted, which is indicated by the padlock icon and the presence of “https” instead of “http” in the address bar. The “s” stands for secure. When you connect to an HTTPS site, the communication between you and the website is encrypted, which makes browsing the web dramatically more secure, protecting your communication from prying eyes and the injection of malicious code. HTTPS is not only used by websites, it also secures the majority of APIs and mobile application backends.
The underlying technology that enables secure communication on the Internet is a protocol called Transport Layer Security (TLS). TLS is an evolution of Secure Sockets Layer (SSL), a protocol developed by Netscape in the 1990s. The Internet Engineering Task Force (IETF), a standards body, has been in charge of defining the protocol, which has gone through several iterations. The last version, TLS 1.2, was standardized in 2008 and is currently supported by the majority of browsers and HTTPS-enabled web services.
TLS 1.2 can be secure when configured correctly, but its age has begun to show. In the last few years, several high-profile attacks have been published that revealed flaws in the protocol. Eight years is a long time in computer security, so the IETF have been working on a new version of the protocol, TLS 1.3, which should be finalized by the end of 2016.
TLS 1.3 is a major overhaul and has two main advantages over previous versions:
- Enhanced security
- Improved speed
Enhanced Security
Most of the attacks on TLS from the last few years targeted vestigial pieces of the protocol left around from the 90s. TLS 1.2 is highly configurable, and vulnerable sites simply failed to disable the older features in hopes of being compatible with old browsers.
TLS 1.3 embraces the “less is more” philosophy, removing support for older broken forms of cryptography. That means you can’t turn on the potentially vulnerable stuff, even if you try. The list of TLS 1.2 features that have been removed is extensive, and most of the exiled features have been associated with high profile attacks. These include:
- RSA key transport — Doesn’t provide forward secrecy
- CBC mode ciphers — Responsible for BEAST, and Lucky 13
- RC4 stream cipher — Not secure for use in HTTPS
- SHA-1 hash function — Deprecated in favor of SHA-2
- Arbitrary Diffie-Hellman groups — CVE-2016-0701
- Export ciphers — Responsible for FREAK and LogJam

CC 2.0 Generic Aqua Mechanical
TLS 1.3 removes the “bad crypto smell” of these legacy features, making it less likely that attacks on previous versions of the protocol will affect TLS 1.3. This streamlining also makes TLS 1.3 much simpler to configure for server operators. A secondary side effect of the update is that the protocol can be made much faster, resulting in a better web browsing experience.
Improved Speed
Fast page load times are critical to the success of web services. Amazon famously found that every additional 100ms of page load time decreases sales by 1%. A major component of page load time is latency: the time it takes to send data between the browser and the web server.
The impact of latency is especially noticeable for:
a) users on mobile devices
b) users that geographically far away from the server
A message from Sydney to New York and back can take over 200ms, enough for humans to notice. Mobile browsing can also increase latency for a connection. Sending a message over a modern 4G mobile network routinely adds over 100ms of latency to requests. On 3G networks, which are still common in Europe, add over 200ms of additional latency. Even home WiFi connections and ISPs add dozens of milliseconds to requests. This additional latency can make mobile browsing feel slow. Unfortunately, encryption can make these slow connections seem slower. TLS 1.3 helps improve this situation.

To send a message to an encrypted site, you must first establish shared cryptographic keys. This process is called a cryptographic handshake. It requires special messages to be sent back and forth between the browser and the website. The TLS handshake happens behind the scenes whenever you connect to an encrypted site with your browser.
With TLS 1.2, two round-trips are needed to complete the handshake before the request can be sent. Accessing a site over a mobile network can add more than half a second to its load time. With TLS 1.3, the initial handshake is cut in half, requiring only one round-trip. That’s like going from a fast station wagon (0-60mph in 10 seconds) to a Tesla Model S (5 seconds).
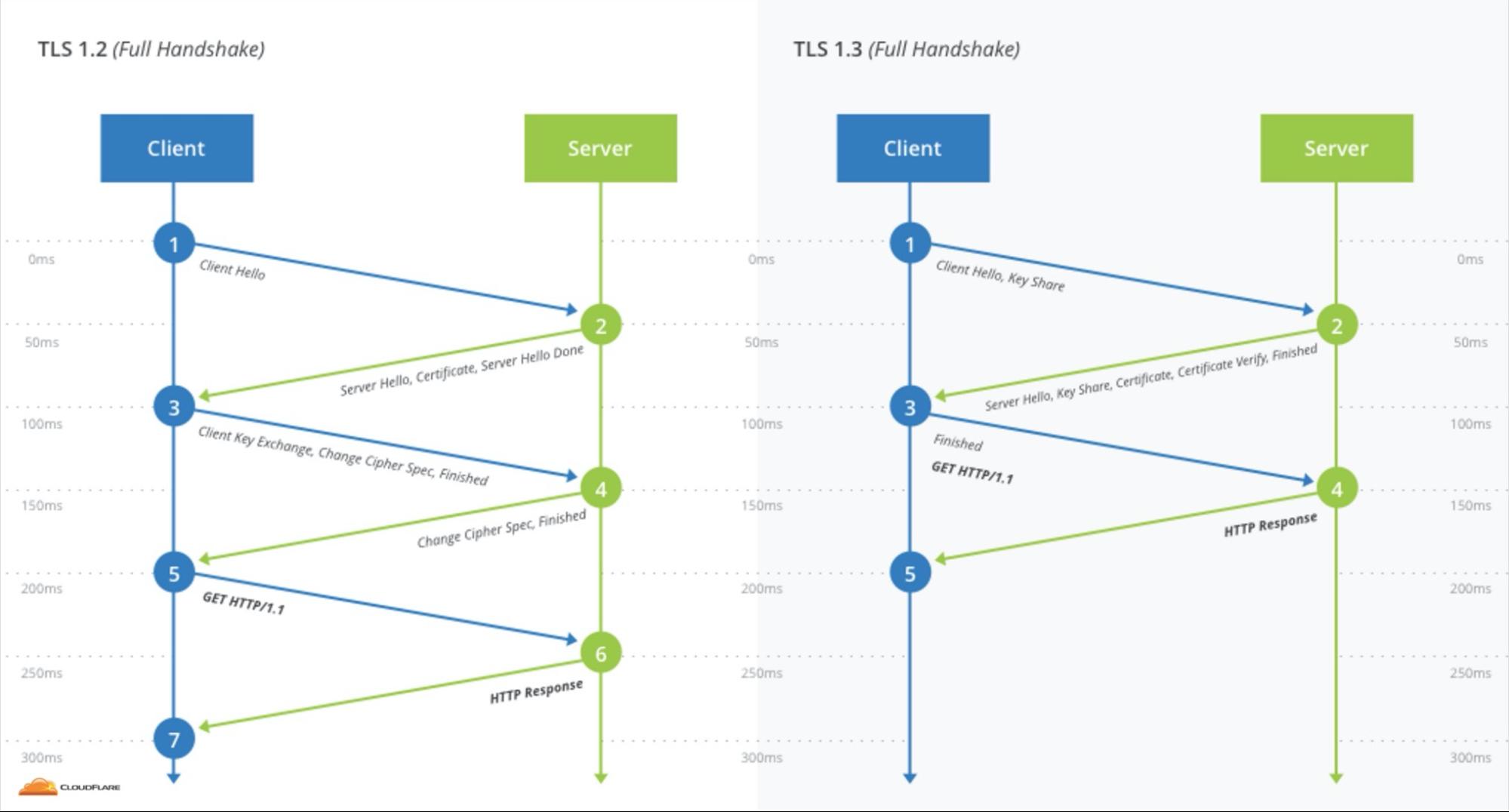
If the round-trip time for a connection is around 100ms, the speed boost from TLS 1.3 is enough to take sites that seem “sluggish” (over 300ms), and turn them into sites that load comfortably fast (under 300ms).
The more efficient handshake is only possible because some of the legacy features present in TLS 1.2 were removed from the protocol. TLS 1.3 also has the additional advantage that for sites you’ve visited recently, you can send data on the first message to the server. This is called “zero round trip” mode (0-RTT) and will result in even faster load times. CloudFlare is planning to support TLS 1.3 0-RTT in the coming weeks.
Live for all
TLS 1.3 is huge step forward for web security and performance. It’s available to all CloudFlare customers, and enabled by default for all Free and Pro customers. You will find the toggle to enable/disable TLS 1.3 in the Crypto tab of the CloudFlare dashboard.
The TLS 1.3 specification is still being polished, but the IETF is very close to settling on a final version of the protocol. Major browser vendors Firefox and Chrome have implemented preliminary versions of TLS 1.3 in their developer releases (Firefox Nightly and Chrome Canary), and we’re updating our implementation to match the current version in these browsers until the specification is final. Expect a faster, safer web browsing experience as more browsers enable TLS 1.3 by default in the coming months.
How to enable TLS 1.3 in your browser
Firefox Nightly
- Install and run Firefox nightly: https://nightly.mozilla.org/
- Enter “about:config” in the address bar
- Set security.tls.version.max from 3 to 4
- Restart the browser
Chrome Canary
- Install and run Chrome Canary: https://www.google.de/chrome/browser/canary.html
- Enter “chrome://flags/” in the address bar
- Go to “Maximum TLS version enabled.” and select “TLS 1.3”
- Restart the browser



No comments yet.