Typos Can have a Bigger Impact Than Expected
Have you ever thought about the cost of a typo? You know what I mean, a simple misspelling of a word somewhere on your website. Do you think there’s a risk in that?
You may have seen the Grammar Police all over your comments yelling that you used the wrong version of “your” and pointing out how stupid you are, right? Unfortunately, that’s the internet. But what if you have misspelled something that your readers can’t see right away?
Gogle API
What if your typo was in some third-party JavaScript? For example, ajax.gogleapis.com instead of ajax.googleapis.com ? There’s a chance that the domain doesn’t exist and the website just breaks, forcing you to spend some time debugging it to find the wrong include. No big deal. But there is a more dangerous possibility here. The domain could be registered and serving malware to those websites.
Luckily enough the owner of ajax.gogleapis.com, Robin Bradshaw, reached out to us with his findings. He posted on Twitter in response to a recent post of ours about the dangers of hosting third-party scripts. Bradshaw told us that he bought the domain because he was bored and wanted to check if those typos were an issue. He got some interesting data.
It is impressive how many hits it has been receiving since February:
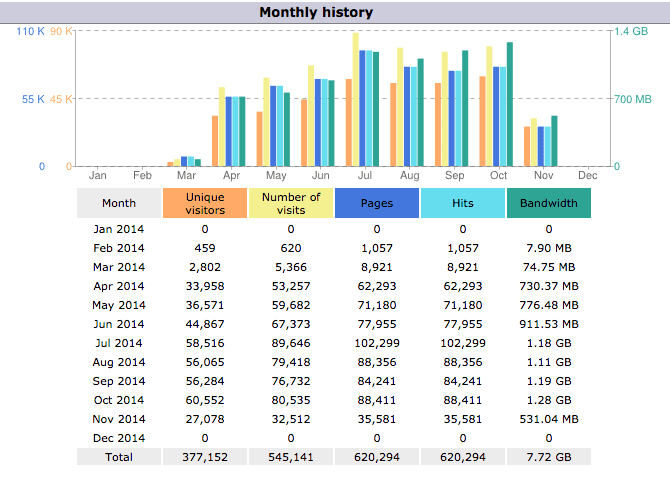
Monthly visits to the misspelled gogleapis.com
Most traffic is coming from Brazilian IP addresses, which is getting there thorough an NGO website. They were contacted to fix this typo, but they never replied. Still waiting for the fix. All the other websites seem to be fixing their code quickly.
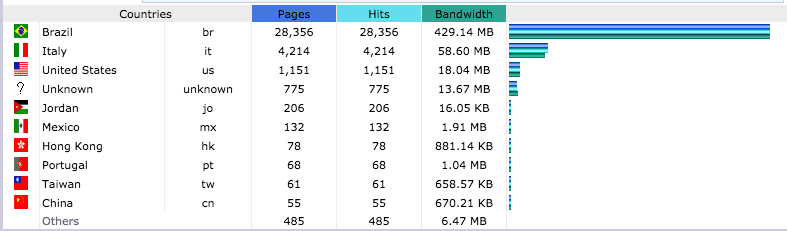
Breakdown of countries using the typos script
Since Bradshaw is such a great guy, not only he did take the typo away from the hands of a person with malicious intentions, but he’s also serving a valid working copy of the ga.js file. Could you imagine how harmful it would be if someone else had gotten a hold of this domain? Someone could easily add to that ga.js file and serve malware or injected malicious SEO.
Typo Squatting
We have looked at one of the possible typos, but what about others?
Of course other people have already thought about using this technique as a way to distribute malware. In this case, the idea is not to register the domain and wait for someone to mistakenly write the URL incorrectly, but rather to deceive the user when they are investigating malicious or suspicious code on their website.
I was able to find a similarly misspelled URL: googleaspis(dot)com. The content is not malicious right now, but it is not serving the right script and it is redirecting the user to a different website.
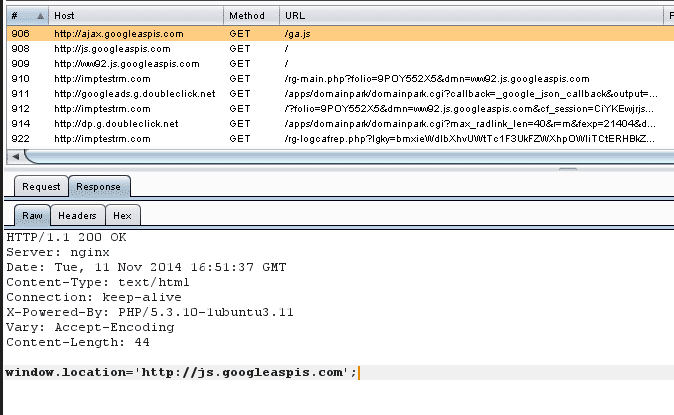
Googleaspis(dot)com Redirects
A quick check on GitHub revealed one repository with a link to this website. Interestingly, the file name was index_malware.html. The website owner probably wasn’t able to find the malware there and recreated the whole index file, but it’s just speculation.
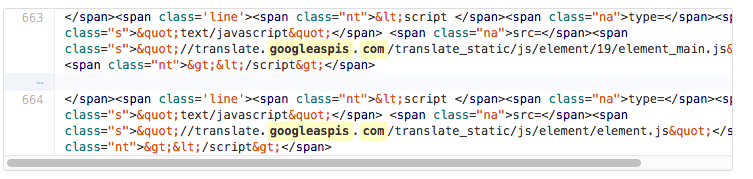
Github shows typo in index_malware.html
There are other typo domains hosted on the same server, like: facebookapis(dot)com, facebboklogin(dot)com, fgoogleapis(dot)com, oogleapis(dot)com and many others.
Conclusion
During my checks I didn’t find any malicious code being hosted by misspelled domains, but that doesn’t mean that there aren’t any. I checked more than 200 variations of Google’s domains used to host scripts for statistics and styles, and all the sites which answered were parked domains. The most suspicious behavior is the one I shared in this post. It does provide for some interesting food for thought though.
Remember to check and double-check all the external content you add to your site. Make sure it’s from a reliable source and that it is typed correctly. The price of a single misspelled character on a domain can be really high.



No comments yet.