Understanding Denial of Service and Brute Force Attacks – WordPress, Joomla, Drupal, vBulletin
Many are likely getting emails with the following subject header Large Distributed Brute Force WordPress Attack Underway – 40,000 Attacks Per Minute. Just this week we put out a post titled More Than 162,000 WordPress Sites Used for Distributed Denial of Service Attack.
What’s the Big Deal?
Remember life before social media? How quiet and content we seemed to be? How the only place we got our information was from the local news or cable outlet? Maybe a phone call, or via email? Today however, we seem to be inundated with information, with raw unfiltered data, left to our thoughts and perceptions of what they really mean. Every day there is some new tragedy, a plane goes missing, a child is abducted, a school shooting, the brink of WWW III. Is it that we live in a time where we are all losing our mind? Or maybe, could it be that the only difference between now and then, is the insane amount of information at our finger tips?
With this in mind, yes, it’s true, there are ongoing Distributed Denial of Service (DDoS) and Brute Force attacks against WordPress sites. In fact it extends far beyond that specific platform, it’s affecting many other platforms like vBulletin, Joomla, Drupal. The reality is that these attacks have been ongoing for many months now, so much so, that they’ve become part of our daily life and it’s not when they happen that we’re surprised, quite the contrary, when they don’t.
Maybe we get too immune to the issues, maybe we don’t do enough to share and provide feedback. It’s likely attributed to the type and scale of the attacks we see, or the breadth of the website landscape we look at. Either way, this post will hopefully get us all talking apples to apples.
Let’s talk about the biggest issues facing website owners to date in 2014 – Distributed Denial of Service (DDoS) and Brute Force attacks.
Denial of Service (DoS) / Distributed Denial of Service (DDoS)
Denial of Service (DoS) attacks and Distributed Denial of Service (DDoS) attacks are the same thing, only thing differentiating the two is scale.
When you hear someone mention a DoS attack, you can expect the attack to be marginal (Qualifier: obviously marginal is very subjective and many would disagree that any DoS is marginal). In most instances, when you hear someone say DDoS, you can think the opposite (i.e., think grand!!).
In either case, whether a DoS or DDoS, the attacker is making use of one or more computers. DoS attacks are on the lower end of that spectrum while DDoS attacks are on the higher end of that spectrum, very large DDoS attacks can span 100′s if not 1,000′s of systems (often all compromised). In fact, many of those compromised servers can be your own website server, ever think of that? There is also the possibility they leverage pingback features such as the one we shared earlier this week.
The principle of a DoS / DDoS attack are very simple. The idea and intent is to disrupt your service, regardless of what it is. The US-CERT (United States Computer Emergency Readiness Team) provides this description:
In a denial-of-service (DoS) attack, an attacker attempts to prevent legitimate users from accessing information or services. By targeting your computer and its network connection, or the computers and network of the sites you are trying to use, an attacker may be able to prevent you from accessing email, websites, online accounts (banking, etc.), or other services that rely on the affected computer. – US CERT
The proliferation of DoS/DDoS attacks is undoubtedly attributed to the ever-growing DDoS-for-hire service market, a.k.a Booter Service, and the media’s infatuation with the scale of such attacks. Brian Krebs wrote an outstanding article on the new norm when it comes to DDoS attacks – 200 – 500 Gbps(GBPS = Gigabytes Per Second). Now that is very large folks. These are not likely the things you, as everyday website owners will be facing though. What you’re more likely to experience are a much smaller scale, think less than 20 GBPS on average.
Don’t be fooled though, the impact and intent are the same – disrupt your website’s daily operation.
Why DDoS a Website?
As for the why, here are a list of reasons we have come up with that best help comprehend why someone would do something like this:
- People bored with nothing better to do.
- Political agenda – Malaysian Elections 2013
- You’ve pissed people off – Brian Krebs – The Researchers Hackers Love to Hate
- You’re in competition with each other
Do you fit into any of them? The odds are that everyone reading this most likely does, at least into one category, and that right there folks is the biggest challenge with addressing a problem this large.
Brute Force Attacks
Now, let’s take a moment to shift our focus to Brute Force attacks.
Brute force attacks, although sharing some similarities with DoS/DDoS attacks, are independent attacks in it of themselves. Their entire focus is completely different from what you would come to expect of DoS / DDoS attacks.
In a Brute Force attack the objective is access to something.
The Open Web Application Security Project (OWASP) group provides us a more eloquent description:
A brute force attack can manifest itself in many different ways, but primarily consists in an attacker configuring predetermined values, making requests to a server using those values, and then analyzing the response. For the sake of efficiency, an attacker may use a dictionary attack (with or without mutations) or a traditional brute-force attack (with given classes of characters e.g.: alphanumeric, special, case (in)sensitive). Considering a given method, number of tries, efficiency of the system which conducts the attack, and estimated efficiency of the system which is attacked the attacker is able to calculate approximately how long it will take to submit all chosen predetermined values. – OWASP
Brute Force Attacks and Websites
The explosion of Content Management Systems (CMS) like WordPress, Joomla, Drupal, etc. have made it such that any person looking to quickly establish a virtual presence is now able to do so with little to no effort. From the platforms perspective this is awesome, right? User adoption, market domination, ease of use, happy consumers? Just look at WordPress with over 20% market dominance in the website industry, impressive I know.
Guess who else thinks it’s impressive, that’s right, the attackers. They realize how the website landscape has changed, it’s no longer combating large organizations with large staff dedicated to security, instead it’s you, small business owners, bloggers, podcasters, readers and writers alike. It’s people who have the need to disseminate information easily and freely. Unlike the times of past, this new breed of website owners care more about their content and it’s distribution than the integrity and security of their website. In fact, if you talk to most website development and design shops you’re likely to get horror stories when it comes to conveying the importance of security to their clients.
This lends itself to Brute Force vulnerabilities. To be clear though, the issue here is not software in these cases, it’s a people thing. You see, when we talk about Brute Forcing what we’re talking about is exploiting a websites access control mechanism (in most cases). When we say access control we’re referring to the websites entry-point (e.g., WordPress – wp-admin / wp-login.php and Joomla – /administrator).
For those that are not technical, imagine walking up to a doorknob and it’s locked. You pull out your awesome key chain, on which you have over 1,000 keys(intense I know), and you proceed to sit there and try every key combination. Yes, I know, highly unrealistic, but what if you could put a robot in your place to go through every combination? Welcome to Brute Force attacks and the web. Not the smartest, but easy and proven to be highly effective.
In its simplest form, this is what attackers are doing. They use tools to pass a combination of user and password information to your websites access control point (think wp-admin / administrator / etc.) in the hope they will get lucky. And by lucky, we mean get access to your website.
Why Brute Force a Website?
As we mentioned before, the intent of Brute Force attacks is fundamentally different from DoS/DDoS attacks. Their primary objective is access.
In the underbelly of the web, access is king. With it, attackers are able to achieve notoriety amongst their peers, achieve huge economical gains and, of course, bring about unjust pain to your virtual presence.
In most instances, the Brute Force attacks are not manual, instead they are being randomly executed by supporting bots, part of larger networks. These bots are configured to randomly crawl the web for preset conditions (i.e. look for URL’s that end with wp-admin). Once the condition is found the attack is unleashed, in many instances it’s not too far to think that the attacker doesn’t even know who they are attacking, that is until the scan responds with a success. How would your website respond if scanned?
Brute Force Attacks – A Look At the Numbers
It’s always easier when we have statistics to work with, so lets stick with WordPress and dive into the last 30 days to see what we can come up with.
We went back 30 days and pulled a list of the Top 40 usernames and passwords being used by attackers on WordPress sites specifically. Over that period we were averaging approximately 15,400 Brute Force attempts a minute, at its peak we were blocking close to 89,400 a minute.
Note: When someone uses the word attack it can be very ambiguous. To help clarify, when we say it in relation to Brute Force and access, we’re referring to attempts against the access point – i.e., wp-admin, wp-login.php, etc…
WordPress currently makes up only 29% of our existing Website Firewall network. The chart below provides a better breakdown of the various platforms in our network.
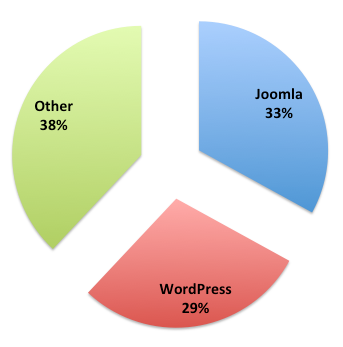
The following images are going to share some specific insights into what we’re seeing. It will provide you a list of commonly used usernames and passwords by attackers. This is important because the attackers do what is most lucrative, in other words showing what is most effective in terms of success rate.
Brute Force – Username Percentage
This pie chart will provide you a complete list of the top 40 usernames attempted during that period, and their percentage dominance. Here are the top 3:
- admin – 84%
- administrator – 4%
- root – 4%
This pie chart shows how overwhelming the percentage is of attacks that use “admin” or “administrator” as the username. Notice the capitalization, it matters.
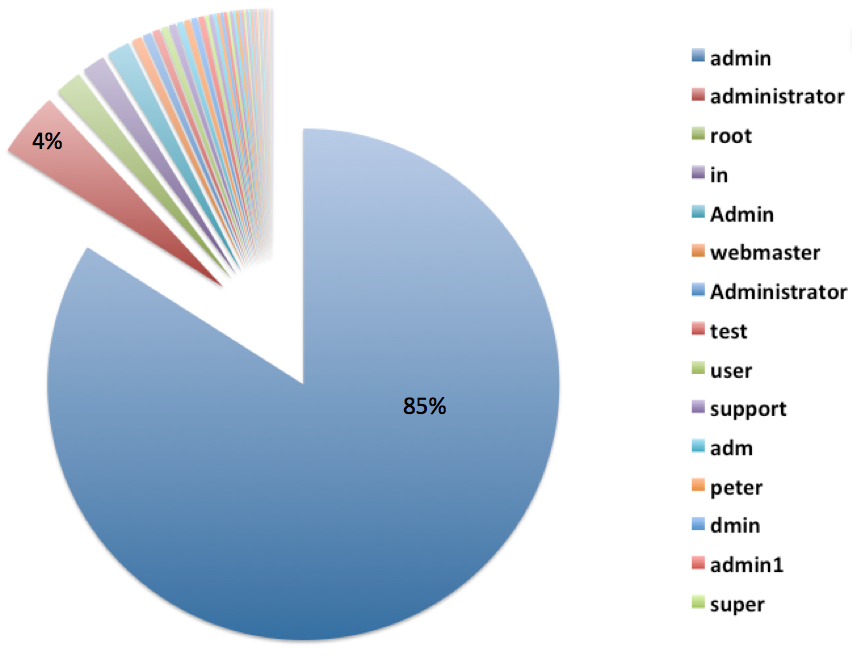
You likely noticed how lopsided the username percentages appear. Why is admin at 84%? Yes, it’s likely this is tightly attributed to its success rate. The flip side to that argument is it’s the most convenient and easiest to apply. Although tools exist that allow an attacker to rotate various username and password combinations, technological limitations do preclude this from happening and as such, unlike local Brute Force attempts, the attackers must be more pragmatic in their tests. This would lead you to believe that the real emphasis comes in passwords.
It’s about low-hanging fruit.
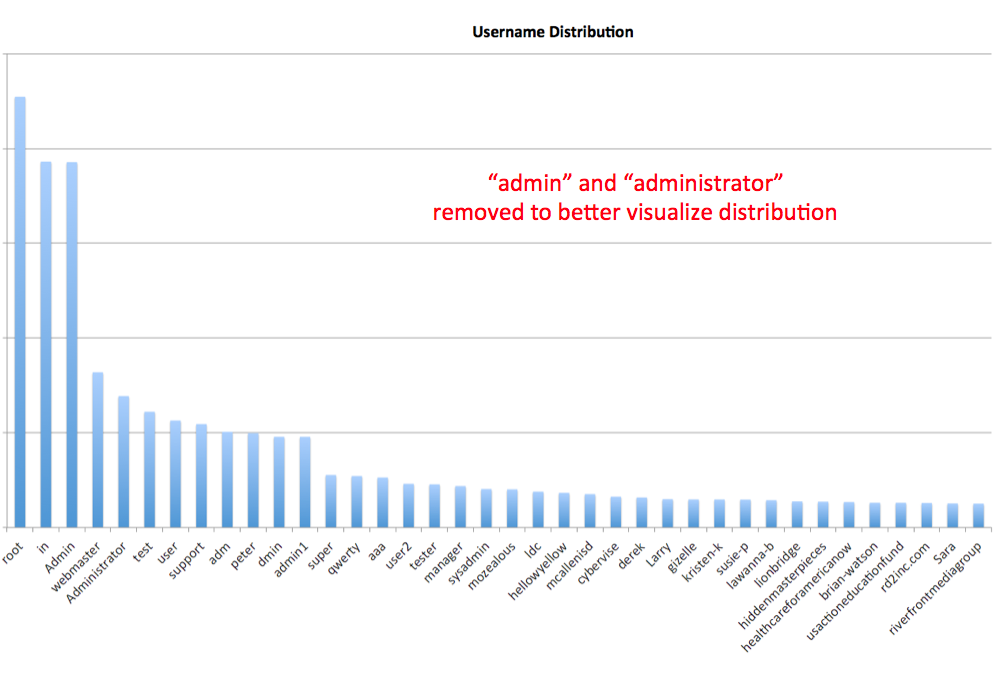
Brute Force – Username Usage Distribution
This table will show you a better illustration of the other usernames being tested, their relationship to the two main culprits, “admin” and “administrator” that we had to remove them from the chart to better illustrate the distribution.
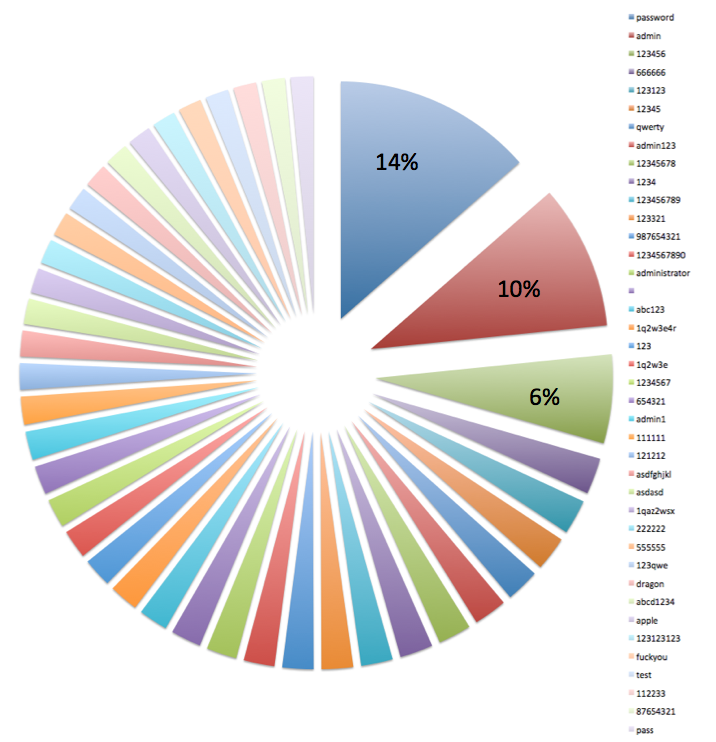
Brute Force – Password Percentage
This pie chart will provide you a complete list of the top 40 passwords attempted during the same period. No surprise to anyone, the top 3 were:
- password – 14%
- admin – 10%
- 123456 – 6%
Technological Advancements
Advancements in technology have made what some thought to be impossible or unrealistic a few years ago, into very real realities today. We no longer have the challenges we did 10 years ago, or even 5, around networks and latency. Today with the explosion of websites, and massive lack of understanding on the principles of running a website, or server, we have created a pool of blood and the sharks are hungry.
This is facilitated by a plethora of hacking toolkits, easily accessible in the darkest and not so dark corners of the web. These tools allow attackers to easily and effectively perform DoS/DDoS attacks and Brute Force attacks easily. While the two types of attacks are fundamentally different, they do share common traits.
The most common trait being the use of compromised environments, both local desktops and web servers. Whether a DoS/DDoS or Brute Force attack, you can rest assured that the odds that the attack is coming from a, what should be clean environment, is very high. Unfortunately, this is a very grave concern, as attacks increase, so do their success rates, and one of their more effective tools continue to be Brute Force for access and DOS / DDoS for service disruption. In either case, scripts are loaded onto servers, existing resources are leveraged and abused, and the end-result is the same – websites are blacklisted, server IP’s are blocked, and website owners, like you, have very miserable days, weeks, months.
The other harsh reality of Brute Force attacks is that they can be synonymous with DOS / DDoS attacks. Although the intent is different, with a BF attack they are after access, disruption is often a very close, and an acceptable second. The DOS byproduct of a Brute Force attack is being facilitated by overloaded shared servers, a majority of what you see today’s websites, and mismanaged web servers that are too small for the traffic they do receive, let alone unexpected surges.
When you ask a website owner, which would you prefer, DDoS or BF attacks? The response is often the same, neither. The problem is, as mentioned above, it’s about scale. Most of you reading this post are not Fortune 100 / 500 companies with large data centers and Network and Security Operation Centers (N/SOC).
The question should not be why me? Instead, let’s focus on how to keep yourself protected…
Protecting Yourself From Brute Force / Denial of Service Attacks</h4
Industries are funny and predictable, the website security space is no different. In comparison to its brother the desktop, it’s an infant, perhaps in its toddler years. What this means is an explosion of services, each adapting to the latest trends reported by organizations like ours. This growth unfortunately causes a great deal of confusion and information overload for many website owners.
The biggest misconception is this idea that local solutions will address or fix the growing dilemma, that is these DoS/DDoS and Brute Force attacks. The reality is, solutions like plugins and extensions don’t and won’t begin to scratch the surface. Just like service providers are jumping on board to build and release solutions, so are the attackers and the problem is growing at a much faster rate than planned, or maybe it’s just becoming more visible.
In the coming months and years, as the problem continues, we’ll continue to see that true success lies in service based Website Firewalls with their own infrastructures, designed to handle these issues. This is not to say however that organizations are not capable of handling it themselves, it’s just that it doesn’t make sense. The real solution comes down to the distribution, segmentation and analysis of the traffic load.
The biggest problem local solutions face, is that they are local. This means their limitations are always going to be tied to their local environment, specifically its resources. This in it of itself already puts most website owners at a disadvantage when you think of resources. Remember the discussion above on scaling and the use of compromised environments?
The other challenge is around intelligence, not human intelligence, but attack and data intelligence. Local solutions are restricted to their immediate field of vision, unless you’re a CNN, Times, etc. the odds of seeing enough information to make and employ appropriate counter measures is not in your favor – this is the harsh reality of the situation.



No comments yet.