MailPoet Vulnerability Exploited in the Wild – Breaking Thousands of WordPress Sites
A few weeks ago we found and disclosed a serious vulnerability on the MailPoet WordPress Plugin. We urged everyone to upgrade their sites immediately due to the severity of the issue. The vulnerability allowed an attacker to inject anything they wanted on the site, which could be used for malware injections, defacement, spam and many more nefarious acts.
This is not something we’re excited to report, but we were right.
A few days ago we started to see a massive number of WordPress sites compromised with malware. The malware code had some bugs, it was breaking many websites, overwriting good files and appending various statements in loops at the end of files.
At the time of the post, the root cause of the malware injections was a bit of a mystery. After a frantic 72 hours, we are confirming that the attack vector for these compromises is the MailPoet vulnerability. To be clear, the MailPoet vulnerability is the entry point, it doesn’t mean your website has to have it enabled or that you have it on the website; if it resides on the server, in a neighboring website, it can still affect your website.
All the hacked sites were either using MailPoet or had it installed on another sites within the same shared account (cross-contamination still matters).
Exploited in the Wild
The attacks always start the same, with the attackers trying to upload a custom (and malicious) theme to the site:
194.79.195.139 – – [05/Jul/2014:01:41:30 -0700] “POST /wp-admin/admin-post.php?page=wysija_campaigns&action=themes HTTP/1.0″ 302 – “http://site.com.com/wp-admin/admin.php?page=wysija_campaigns&id=1&action=editTemplate” “Mozilla/5.0″
Once they succeed, they upload the malicious theme, they access their backdoor inside /wp-content/uploads/wysija/themes/mailp/:
194.79.195.139 – – [05/Jul/2014:01:41:31 -0700] “GET /wp-content/uploads/wysija/themes/mailp/index.php HTTP/1.1″ 200 12 “Mozilla/5.0″
194.79.195.139 – – [05/Jul/2014:04:08:16 -0700] “GET /wp-content/uploads/wysija/themes/mailp/index.php?cookie=1 HTTP/1.0″ 200 12 “-” “Mozilla/5.0 (Windows)”
They get full control of the site.
The Backdoor is very nasty and creates an admin user called 1001001. It also injects a backdoor code to all theme/core files. The biggest issue with this injection is that it often overwrites good files, making very hard to recover without a good backup in place.
So if you see this error on a site:
Parse error: syntax error, unexpected ‘)’ in /home/user/public_html/site/wp-config.php on line 91
It means it was likely hacked through this vulnerability.
Mass Infections
MailPoet is a very popular plugin with almost 2 million downloads, so as you can expect, when such severe vulnerability is identified, it can be mass exploited.
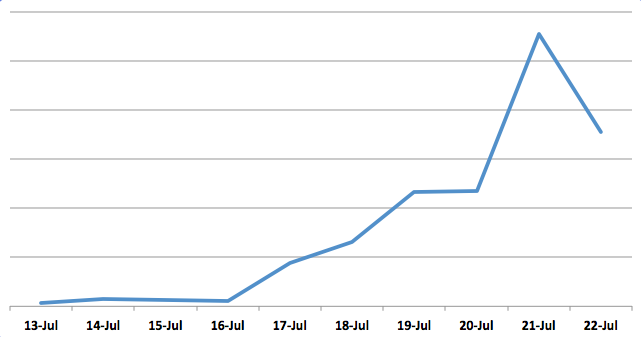
This is the total number of hacked sites that we were able to identify so far (per day):
This is based on sites scanned on our free sitecheck scanner. The number of hacked sites is likely much bigger.
Upgrade Mailpoet!
If you are running MailPoet, we recommend upgrading it asap to the latest version. Users of our Website Firewall (CloudProxy) have been protected against this threat since day 0. However, if you do not have a firewall (WAF) on your website, you have to upgrade the plugin or remove it altogether to avoid more issues.



No comments yet.