Website Malware – Curious .htaccess Conditional Redirect Case
I really enjoy when I see different types of conditional redirects on compromised sites. They are really hard to detect and always lead to interesting investigations. Take a look at this last one we identified:
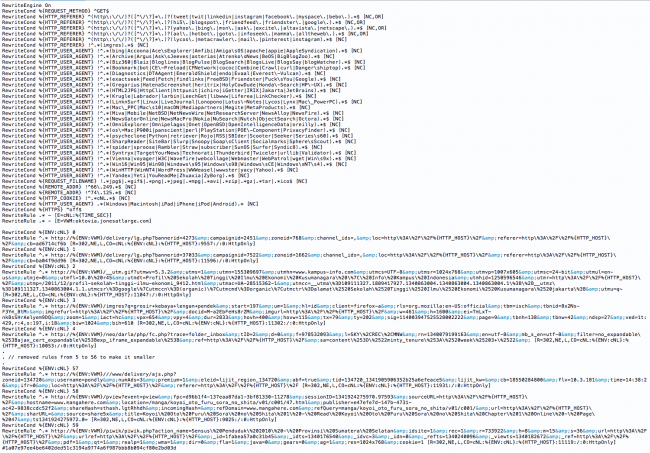
The curious aspect about it is the usage of a not so common .htaccess feature: variables. Most conditional injections rely only on the user agent (browser) or referer of the visitor, but this one also leveraged the TIME_SEC and VWM variables:
RewriteRule .* - [E=cNL:%{TIME_SEC}]
RewriteRule .* - [E=VWM:oktovia.jonesatlarge.com]
It’s attributing the TIME_SEC (the “seconds” part of current time) to the cNL variable and the payload to VWM. It causes the malware to redirect the visitor to a different page, depending on the time of the day.
For example, if it is 9:00:01 (ending in the “01” second), it will redirect the visitor to a specific campaign ID (7522). If it is 9:00:02 (ending in the “02” second), it will redirect to a different campaign ID, and so on until it reaches all 60 seconds.
And when you mix that with all other conditions that this .htaccess malware has:
- It checks if the referer came from Google, Facebook, Twitter and a few other popular sites.
- It checks if the operating system is a Mac, Windows, iPhone, iPad, iPod or Android
- It checks if the cookie cNL is not set (to prevent displaying the malware more than once to the same person.
- It checks the time of the request to build a custom URL depending on the second.
It becomes very hard to be detected and even hard to get all malicious URL’s identified.
Very sneaky…



No comments yet.