2014 Website Defacements
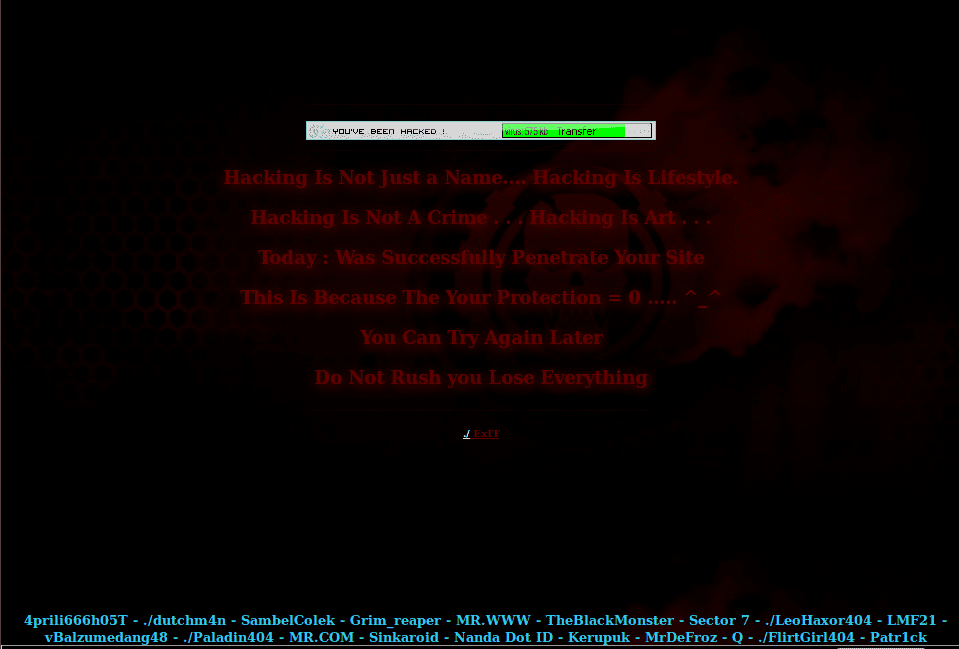
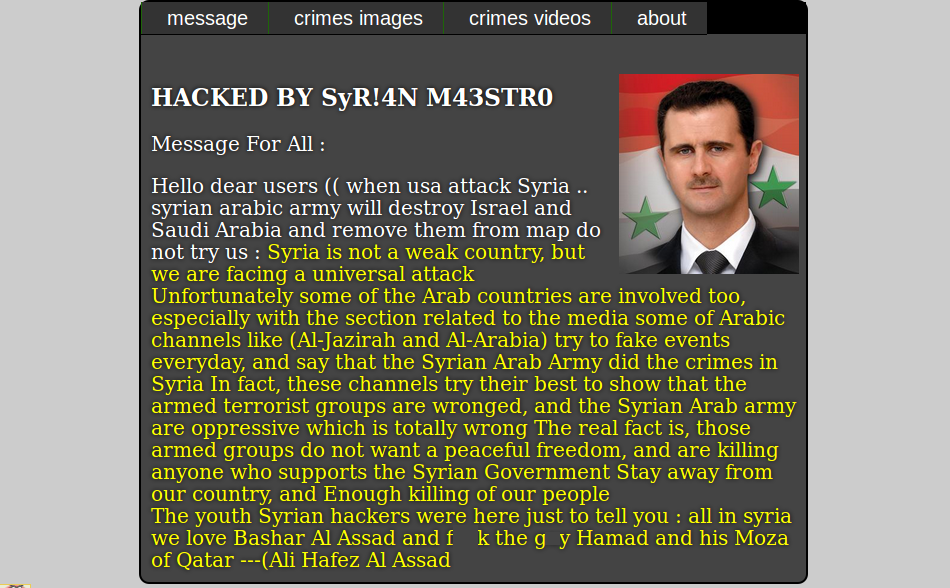
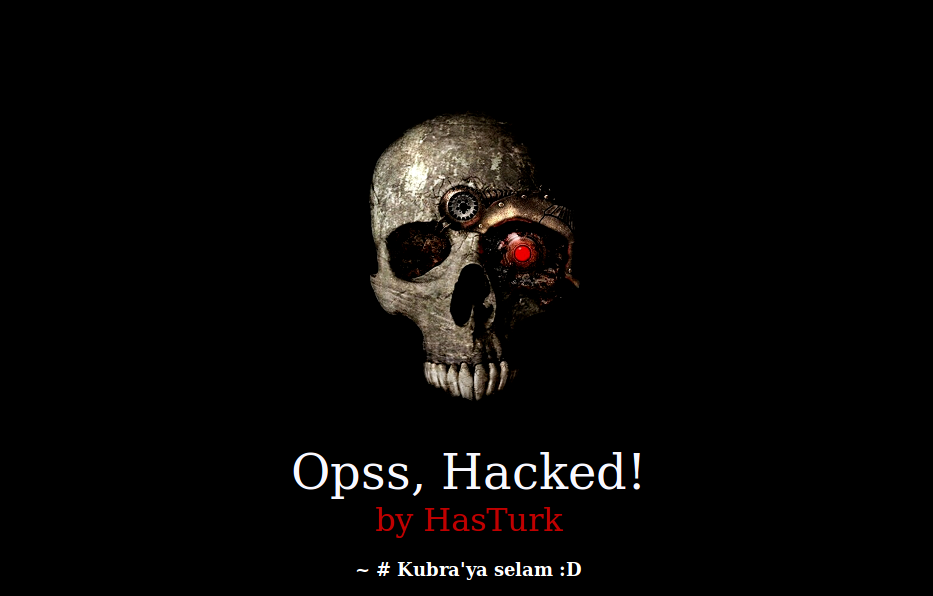
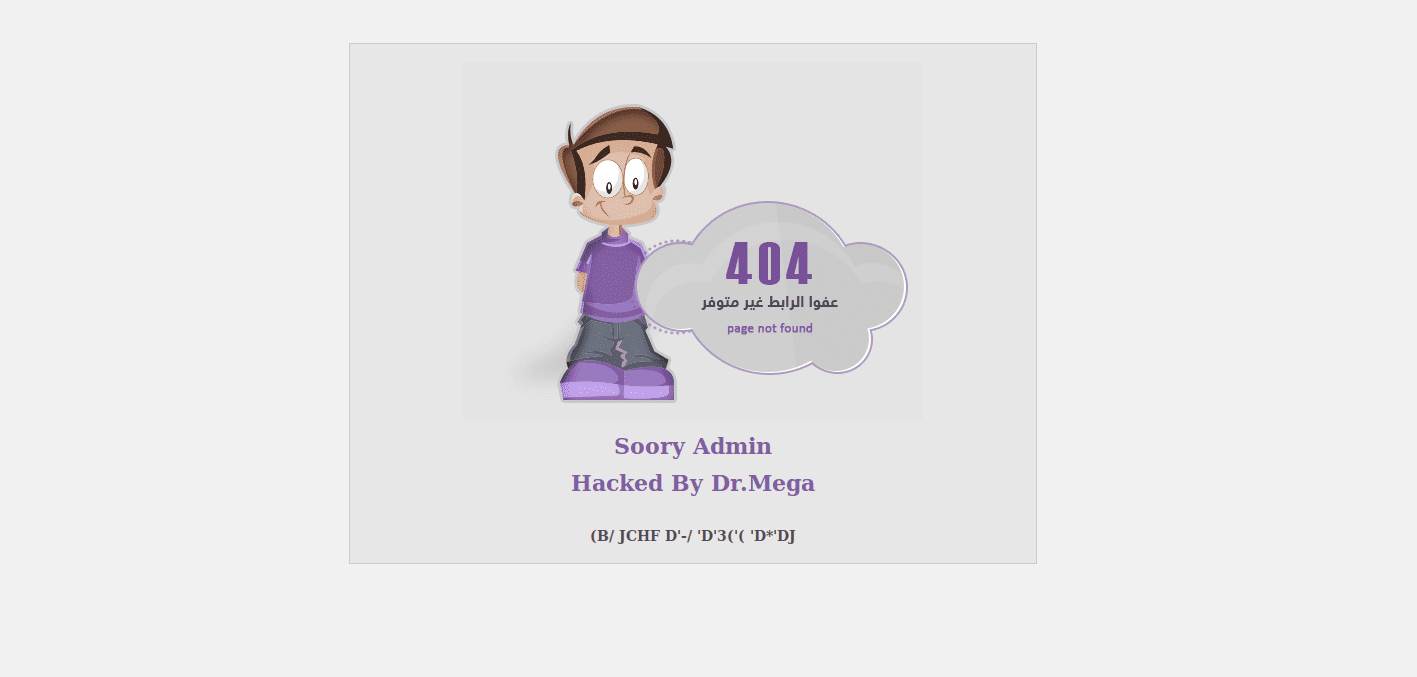
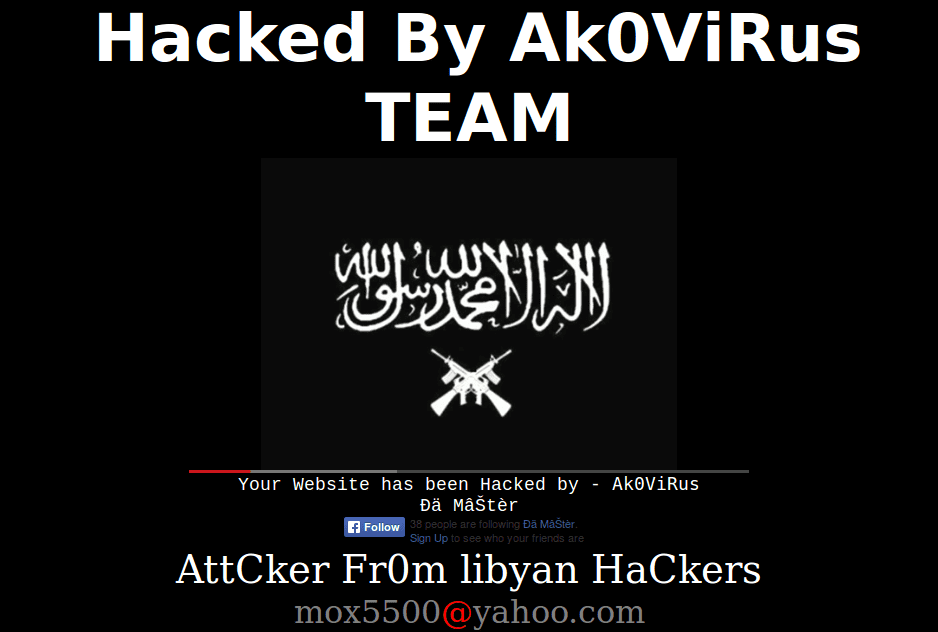
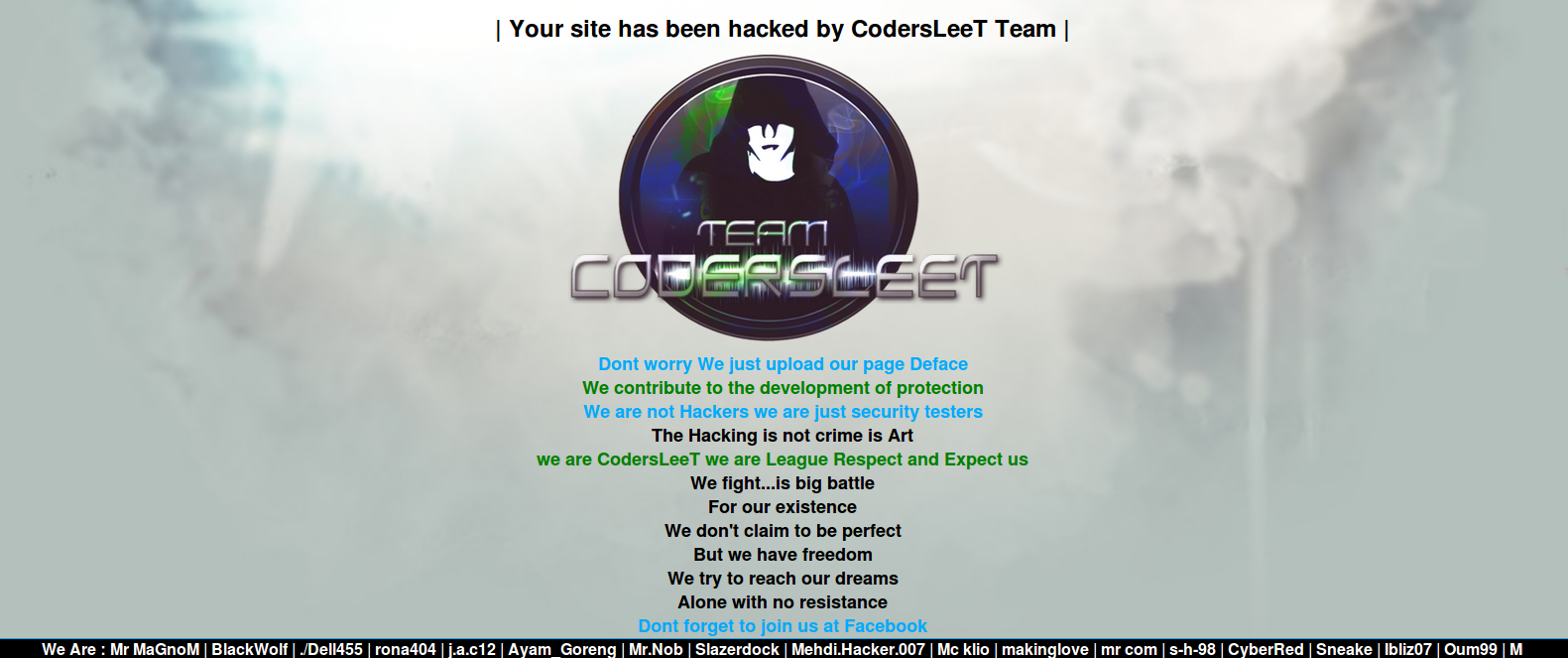
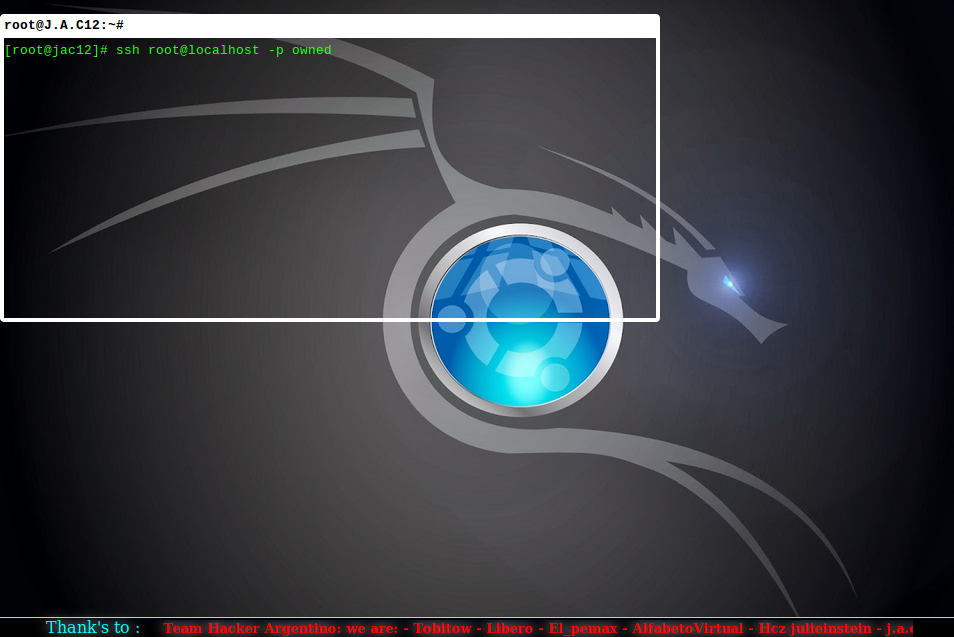
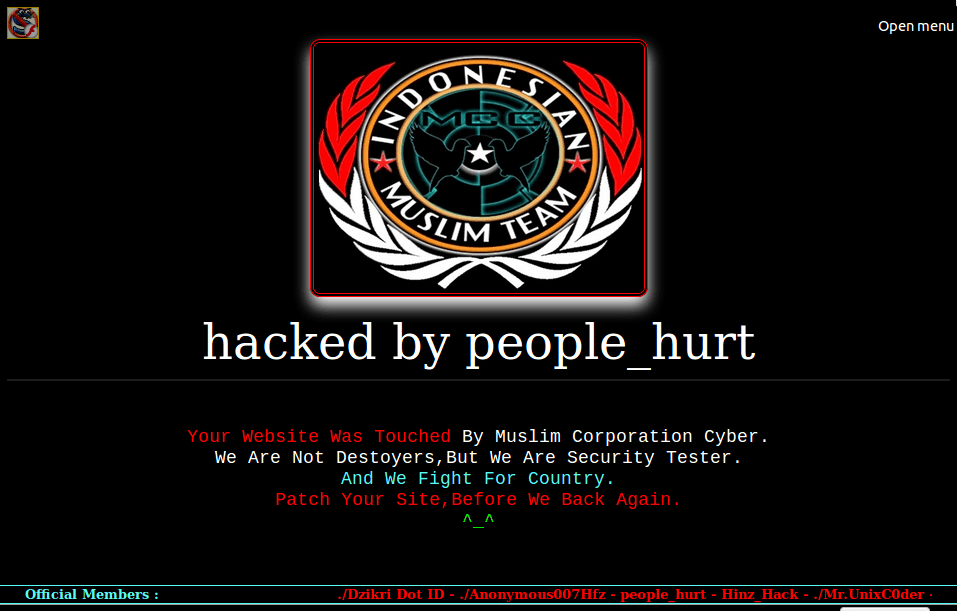
Defacements are the most visual and obvious hack that a website can suffer from. They also come parcelled with their own exquisite sense of dread. Nothing gives that gut-wrenching feeling of “I’ve been hacked” more than seeing this:
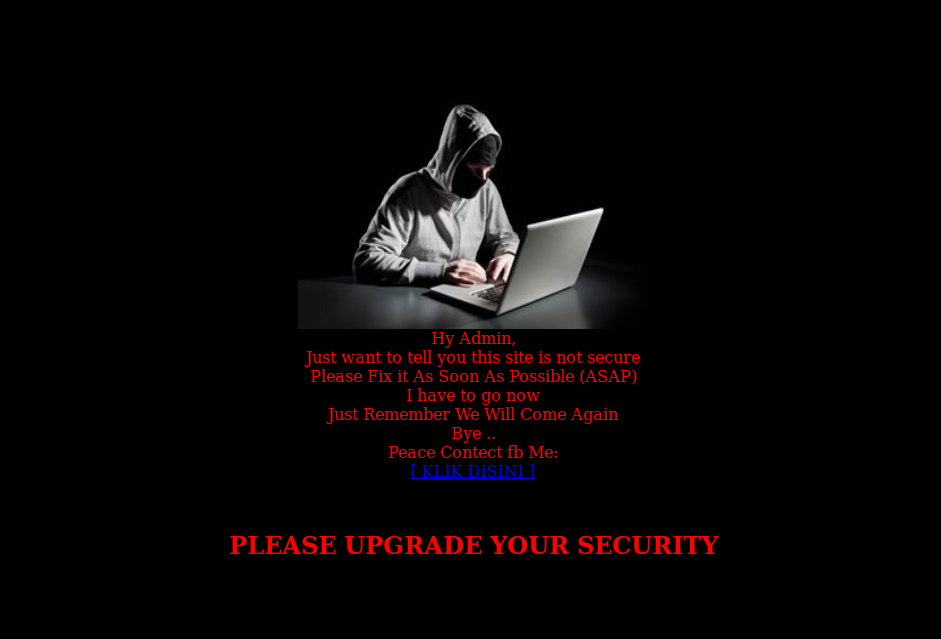
Most malware that we see on a daily basis is driven by some desire to profit off of victims – classic pharma spam or theft of credit card details and personal information. By contrast, most defacements have little to no financial incentive. They are almost always done to further some political, religious or ideological goal. Some attackers will try to deface as many sites as possible with their ‘calling card’ just to prove how “l33t” (elite) they are or to give attention to whatever cause they are trumpeting.
It’s worth mentioning that I am unsure how defacing bobswidgetshop.com furthers any goal at all, nor is defacing a site a tremendously difficult or l33t venture, but I digress.
These hacks remind me of by-gone days when computer hacking was done primarily for mischief and trouble-making and less associated with the nefarious criminal underworld. A lot of the time all that is tampered with is the site’s index.php file which can easily be restored by downloading a fresh copy of whatever CMS you use.
A more nasty defacement, though, will overwrite your wp-config.php file entirely and if you don’t have a backup, well, make one right now for a rainy day ![]()
Now, having said all this, while all defacements are primarily about the shock value much of the time they are coupled with malware, too. If this ever happens to your site assume it is fully compromised and act accordingly. Whoever defaces a site will almost certainly place a few backdoors for easy access later on. The more harmful hacks will also attempt to infect end user computers visiting the site.
For this reason, if you ever suffer from this sort of calamity make sure you perform a thorough check for any malicious files! Otherwise you’ll likely end up with the same problem soon after.
There are a whole bunch of ways that this can happen – websites that employ poor password management and/or use out of date software are easy, low-hanging fruit for these vandalists. Naturally, our clients using our CloudProxy firewall are protected against such attacks.
In conclusion, please enjoy the following slide-show entitled “Gallery of a Web Admin’s Tears”


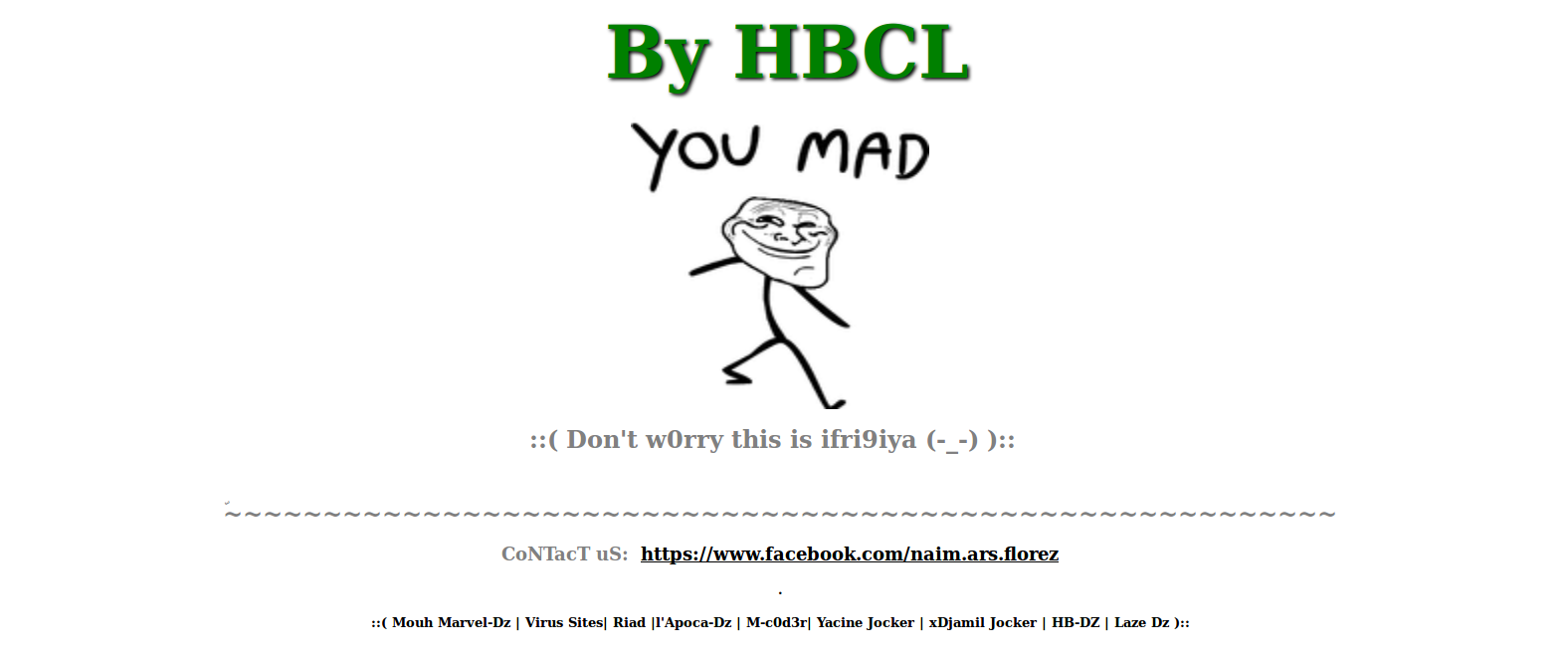
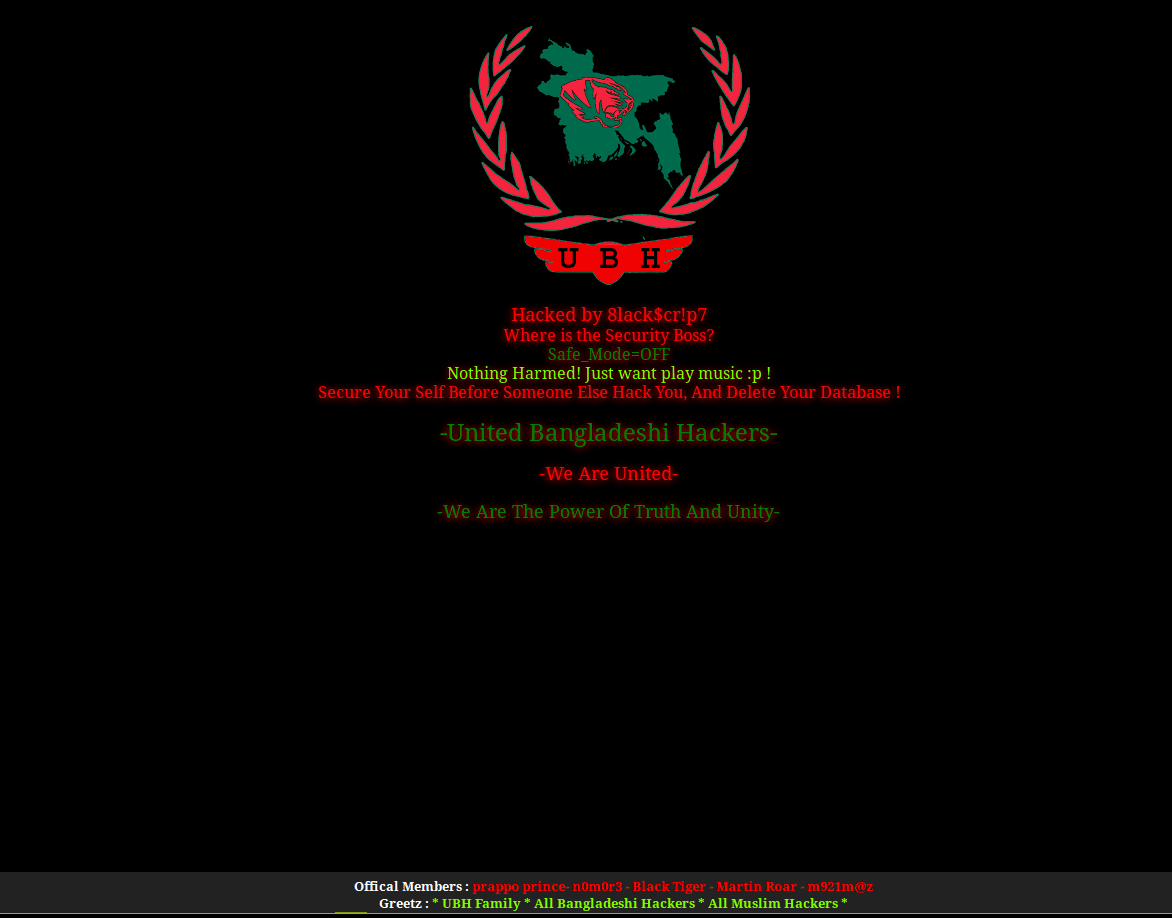
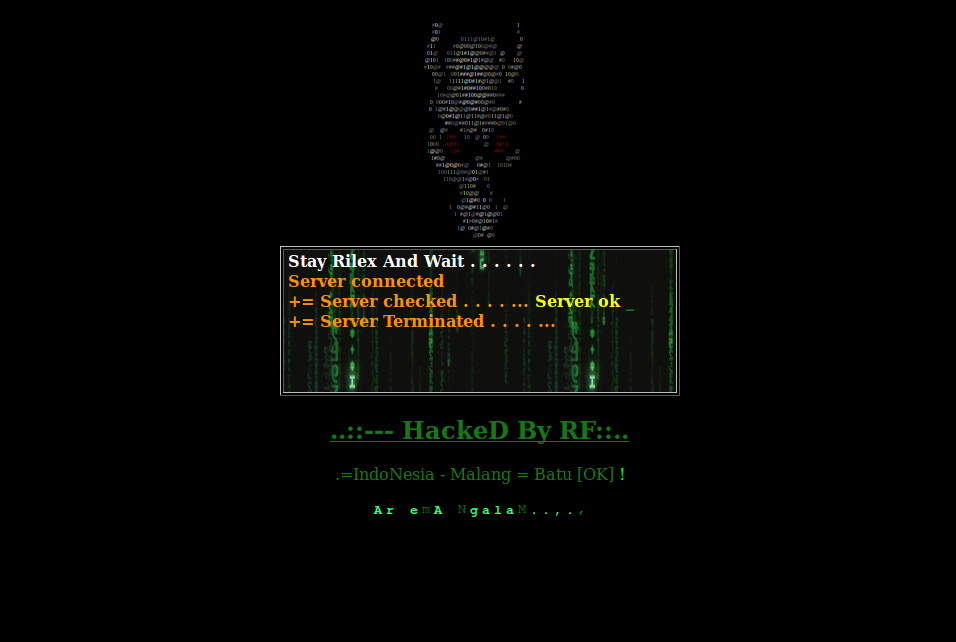













No comments yet.