Phishing Tale: An Analysis of an Email Phishing Scam
Phishing scams are always bad news, and in light of the Google Drive scam that made the rounds again last week, we thought we’d tell the story of some spam that was delivered into my own inbox because even security researchers, with well though-out email block rules, still get SPAM in our inboxes from time to time.
Here’s where the story begins:
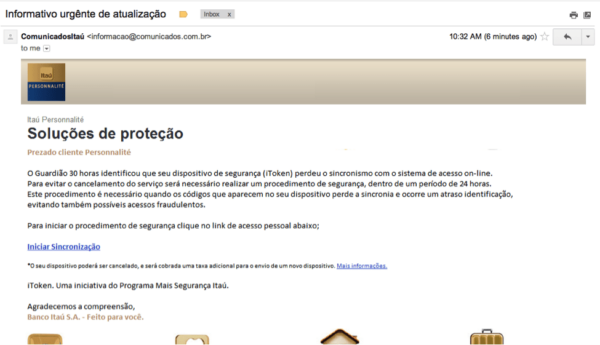
Today, among all the spam that I get in my inbox, one phishing email somehow made its way through all of my block rules.
I decided to look into it a little further. Of course, I wanted to know whether or not we were already blocking the phishing page, but I also wanted to investigate further and see if I could figure out where it came from. Was it from a compromised site or a trojanized computer?
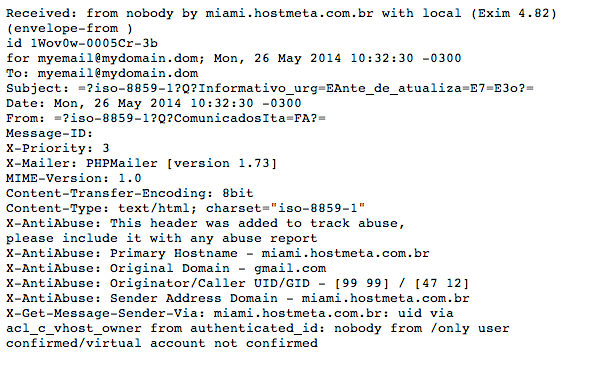
The investigation started with the mail headers (identifying addresses have been changed, mostly to protect my email ☺):
The headers tell us that miami.hostmeta.com.br is being used to send the spam. It’s also an alert that some of the sites in this shared server are likely vulnerable to the form: X-Mailer: PHPMailer [version 1.73]. I decided to look into the server and found that it contained quite a few problems. This server hosts about twenty sites, some of which are outdated–WordPress 2.9.2 is the oldest–while others are disclosing outdated web server versions (Outdated Web Server Apache Found: Apache/2.2.22) and still others are blacklisted (http://www.siteadvisor.com/sites/presten.com.br). This makes it pretty difficult to tell where the spam came from, right?
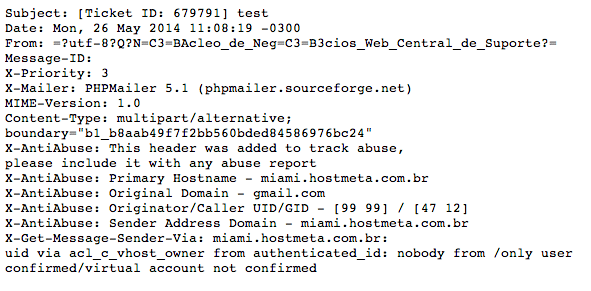
Luckily, there’s another header to help us, Message-ID:. nucleodenegociosweb.com.br is hosted on miami.hostmeta.com.br and it has an open contact form. I used it to send a test message and although the headers are similar, the PHPMailer differs:
What Do We Know Now?
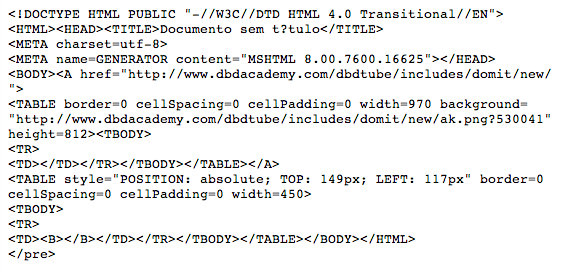
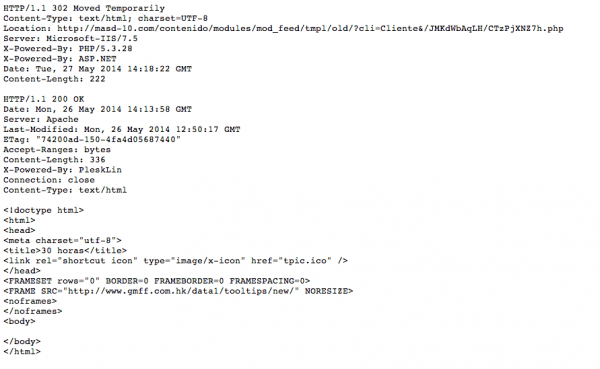
We know who is sending the phishing messages, but what host are they coming from? There are some clues in the message body:
From that image, we can see that http://www.dbdacademy.com/dbdtube/includes/domit/new/ is hosting the image and the link to the phishing scam, but it doesn’t end there. As you can see from the content below, we’ll be served a redirect to http://masd-10.com/contenido/modules/mod_feed/tmpl/old/?cli=Cliente&/JMKdWbAqLH/CTzPjXNZ7h.php, which loads an iframe hosted on http://www.gmff.com.hk/data1/tooltips/new/.
Problem Solved. Or is It?
In this case, there are three compromised sites being used to deliver the phishing campaign and it’s becoming very common to see this strategy adopted. The problem, from the bad guy’s point of view, is that if they store all of their campaign components on one site, then they lose all of their work when we come in and clean the website. If they split the components up and place them on multiple sites, with different site owners, then it’s unlikely that all of the sites will be cleaned at one time, which means their scam can continue. As always with malware, it’s not enough for your site to be clean. You also need to rely on everyone else to keep their own site clean. When others don’t, your computer or website can be put at risk.



No comments yet.