Top 50 Most Impersonated Brands in phishing attacks and new tools you can use to protect your employees from them


Someone in your organization may have just submitted an administrator username and password for an internal system to the wrong website. And just like that, an attacker is now able to exfiltrate sensitive data.
How did it all happen? A well crafted email.
Detecting, blocking, and mitigating the risks of phishing attacks is arguably one of the hardest challenges any security team is constantly facing.
Starting today, we are opening beta access to our new brand and anti-phishing tools directly from our Security Center dashboard, allowing you to catch and mitigate phishing campaigns targeting your organization even before they happen.
The challenge of phishing attacks
Perhaps the most publicized threat vector over the past several months has been phishing attacks. These attacks are highly sophisticated, difficult to detect, becoming more frequent, and can have devastating consequences for businesses that fall victim to them.
One of the biggest challenges in preventing phishing attacks is the sheer volume and the difficulty of distinguishing legitimate emails and websites from fraudulent ones. Even when users are vigilant, it can be hard to spot the subtle differences that attackers use to make their phishing emails and websites look convincing.
For example, last July our Cloudflare One suite of products and use of physical security keys thwarted the sophisticated “Oktapus” phishing attack targeting Cloudflare employees. The attacker behind the “Oktapus” attack that successfully compromised more than one hundred companies, registered the “cloudflare-okta.com” domain name just 40 minutes before sending it to our employees.
At that time, we identified phishing domains with our secure registrar product—but there was a delay in receiving the list of newly registered domains for monitoring purposes. Today, by streaming newly observed domains resolved by our 1.1.1.1 resolver (and other resolvers), we are able to detect phishing domains almost immediately. This gives us the upper hand and allows us to block phishing attempts before they happen.
We want to start giving our customers access to the same tools we use internally, to help you fight the ongoing challenge.
New Brand and Phishing Protection tools in Cloudflare’s Security Center
We’re expanding the phishing protections available to Cloudflare One customers by automatically identifying—and blocking—so-called “confusable” domains. Common misspellings (clodflare.com) and concatenation of services (cloudflare-okta.com) are often registered by attackers to trick unsuspecting victims into submitting private information such as passwords, and these new tools provide an additional layer of protection against such attempts.
The new Brand and Phishing Protection tools can be found under the Cloudflare Security Center, and provide even more controls (e.g. custom strings to monitor, searchable list of historical domains, etc.) to our customers. Cloudflare One plans can have access, with the level of control, visibility, and automation based on their plan type.
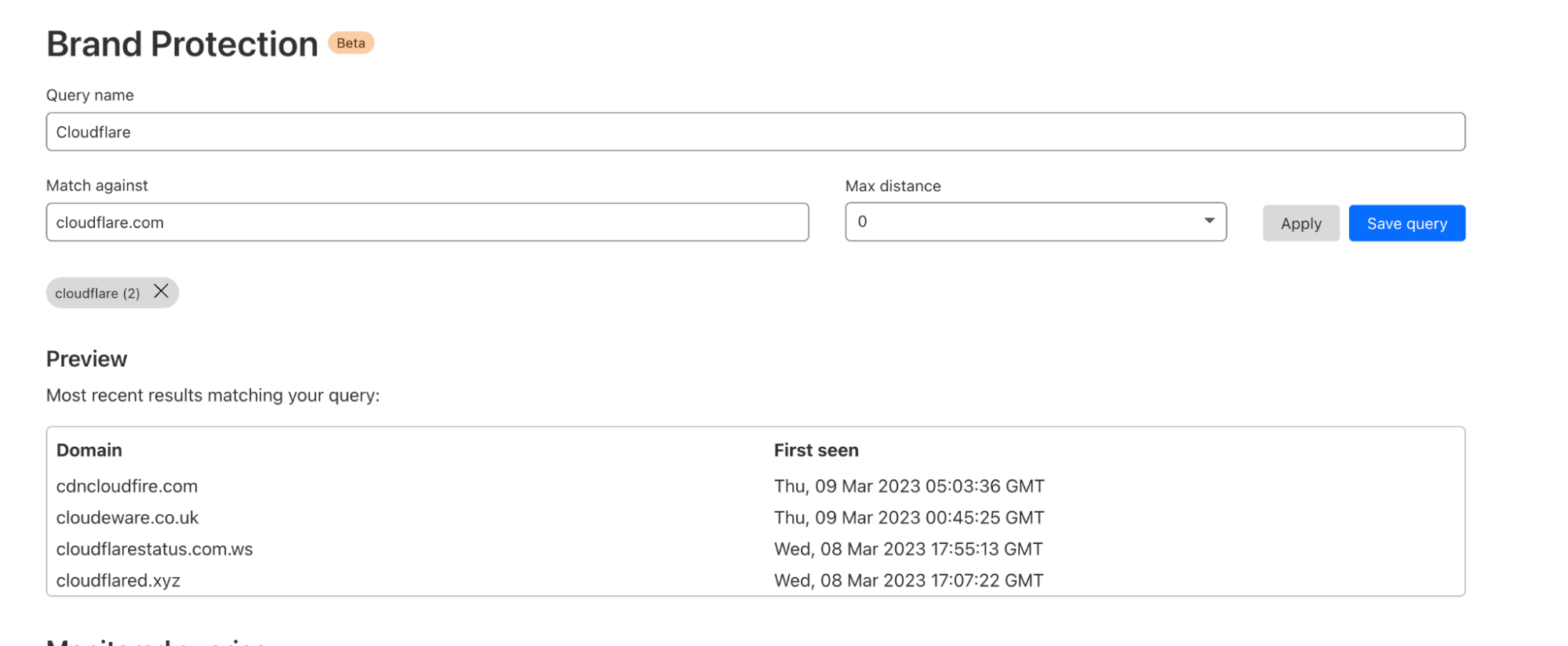
New domain brand matching and alerting
At the heart of our new brand protection feature is our ability to detect hostnames created specifically for phishing legitimate brands. We start by monitoring the first use of a domain or subdomain by sifting through trillions of daily DNS queries made to 1.1.1.1, Cloudflare’s public DNS resolver, in order to compile a list of hostnames in the wild for the first time.
Using this list, we perform ”fuzzy” matching, a technique used to match two strings that are similar in meaning or spelling, against our users’ saved patterns in real-time. We compare the strings and calculate a similarity score based on various factors (ie: phonetics, distance, substring matching). These saved patterns, which can be strings with edit distances, enable our system to generate alerts whenever we detect a match with any of the domains in the list.
While our users currently have to create and save these queries, we will introduce an automated matching system in the future. This system will simplify the process of detecting matches for our users, though custom strings will still be available for security teams tracking more complex patterns.
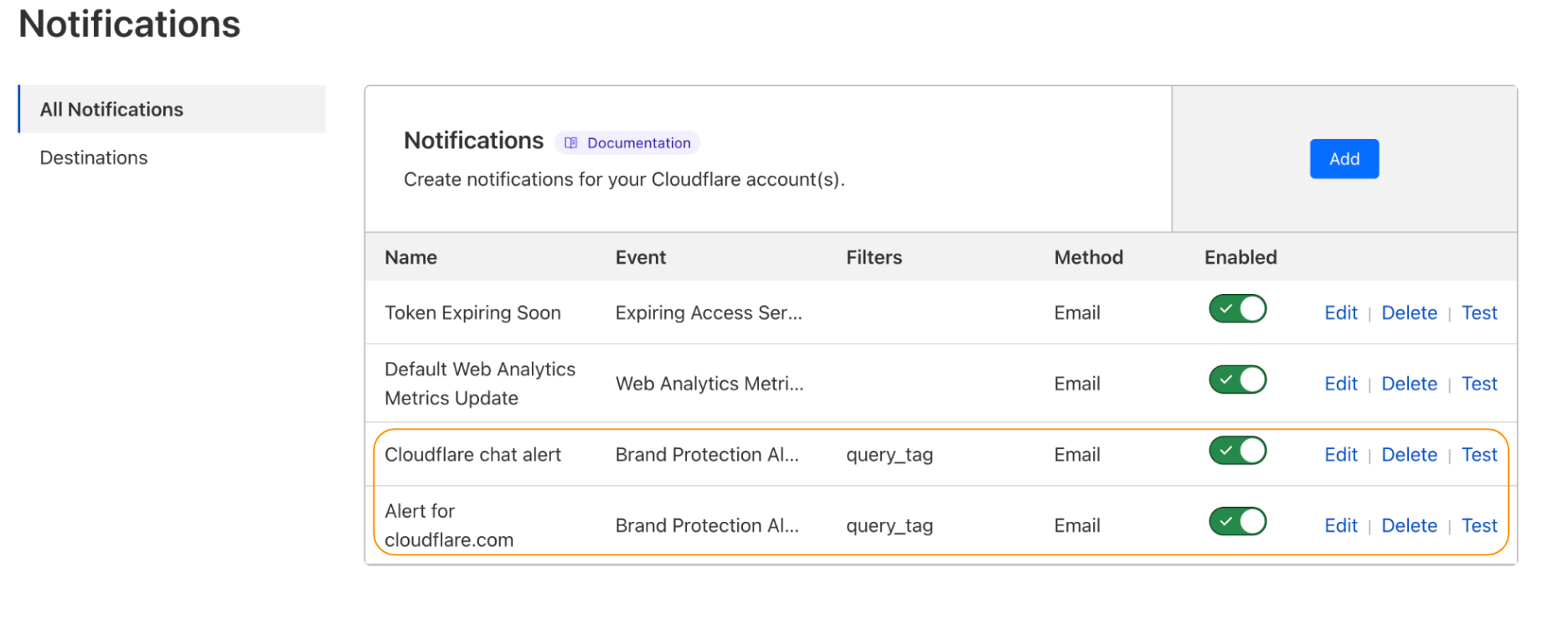
Historical searches
In addition to real-time monitoring, we offer historical searches (saved queries) and alerts for newly observed domains within the last 30 days. When a new pattern is created, we will display search results from the last 30 days to show any potential matches. This allows security teams to quickly assess the potential threat level of a new domain and take necessary actions.
Furthermore, this search mechanism can also be used for ad hoc domain hunting, providing additional flexibility for security teams who may need to investigate specific domains or patterns.
Observations in the wild: most phished brands
While building out these new Brand Protection tools, we wanted to test our capabilities against a broad set of commonly phished brands. To do so, we examined the frequency that domains containing phishing URLs were resolved against our 1.1.1.1 resolver. All domains that are used for shared services (like hosting sites Google, Amazon, GoDaddy) that could not be verified as a phishing attempt were removed from the data set.
The top 50 brands we found, along with one of the most commonly used domains for phishing those brands can be found in the table below.
.tg {border-collapse:collapse;border-color:#ccc;border-spacing:0;}
.tg td{background-color:#fff;border-color:#ccc;border-style:solid;border-width:1px;color:#333;
font-family:Arial, sans-serif;font-size:14px;overflow:hidden;padding:10px 5px;word-break:normal;}
.tg th{background-color:#f0f0f0;border-color:#ccc;border-style:solid;border-width:1px;color:#333;
font-family:Arial, sans-serif;font-size:14px;font-weight:normal;overflow:hidden;padding:10px 5px;word-break:normal;}
.tg .tg-1wig{font-weight:bold;text-align:left;vertical-align:top}
.tg .tg-lqy6{text-align:right;vertical-align:top}
.tg .tg-0lax{text-align:left;vertical-align:top}
| Rank | Brand | Sample domain used to phish brand[1] |
|---|---|---|
| 1 | AT&T Inc. | att-rsshelp[.]com |
| 2 | PayPal | paypal-opladen[.]be |
| 3 | Microsoft | login[.]microsoftonline.ccisystems[.]us |
| 4 | DHL | dhlinfos[.]link |
| 5 | Meta | facebookztv[.]com |
| 6 | Internal Revenue Service | irs-contact-payments[.]com |
| 7 | Verizon | loginnnaolcccom[.]weebly[.]com |
| 8 | Mitsubishi UFJ NICOS Co., Ltd. | cufjaj[.]id |
| 9 | Adobe | adobe-pdf-sick-alley[.]surge[.]sh |
| 10 | Amazon | login-amazon-account[.]com |
| 11 | Apple | apple-grx-support-online[.]com |
| 12 | Wells Fargo & Company | connect-secure-wellsfargo-com.herokuapp[.]com |
| 13 | eBay, Inc. | www[.]ebay8[.]bar |
| 14 | Swiss Post | www[.]swiss-post-ch[.]com |
| 15 | Naver | uzzmuqwv[.]naveicoipa[.]tech |
| 16 | Instagram (Meta) | instagram-com-p[.]proxy.webtoppings[.]bar |
| 17 | WhatsApp (Meta) | joingrub-whatsapp-pistol90[.]duckdns[.]org |
| 18 | Rakuten | rakutentk[.]com |
| 19 | East Japan Railway Company | www[.]jreast[.]co[.]jp[.]card[.]servicelist[].bcens[.]net |
| 20 | American Express Company | www[.]webcome-aexp[.]com |
| 21 | KDDI | aupay[.]kddi-fshruyrt[.]com |
| 22 | Office365 (Microsoft) | office365loginonlinemicrosoft[.]weebly[.]com |
| 23 | Chase Bank | safemailschaseonlineserviceupgrade09[.]weebly[.]com |
| 24 | AEON | aeon-ver1fy[.]shop |
| 25 | Singtel Optus Pty Limited | myoptus[.]mobi |
| 26 | Coinbase Global, Inc. | supp0rt-coinbase[.]com |
| 27 | Banco Bradesco S.A. | portalbradesco-acesso[.]com |
| 28 | Caixa Econômica Federal | lnternetbanklng-caixa[.]com |
| 29 | JCB Co., Ltd. | www[.]jcb-co-jp[.]ascaceeccea[.]ioukrg[.]top |
| 30 | ING Group | ing-ingdirect-movil[.]com |
| 31 | HSBC Holdings plc | hsbc-bm-online[.]com |
| 32 | Netflix Inc | renew-netflix[.]com |
| 33 | Sumitomo Mitsui Banking Corporation | smbc[.]co[.]jp[.]xazee[.]com |
| 34 | Nubank | nuvip2[.]ru |
| 35 | Bank Millennium SA | www[.]bankmillenium-pl[.]com |
| 36 | National Police Agency Japan | sun[.]pollice[.]xyz |
| 37 | Allegro | powiadomienieallegro[.]net |
| 38 | InPost | www.inpost-polska-lox.order9512951[.]info |
| 39 | Correos | correosa[.]online |
| 40 | FedEx | fedexpress-couriers[.]com |
| 41 | LinkedIn (Microsoft) | linkkedin-2[.]weebly[.]com |
| 42 | United States Postal Service | uspstrack-7518276417-addressredelivery-itemnumber.netlify[.]app |
| 43 | Alphabet | www[.]googlecom[.]vn10000[.]cc |
| 44 | The Bank of America Corporation | baanofamericase8[.]hostfree[.]pw |
| 45 | Deutscher Paketdienst | dpd-info[.]net |
| 46 | Banco Itaú Unibanco S.A. | silly-itauu[.]netlify[.]app |
| 47 | Steam | gift-steam-discord[.]com |
| 48 | Swisscom AG | swiss-comch[.]duckdns[.]org |
| 49 | LexisNexis | mexce[.]live |
| 50 | Orange S.A. | orange-france24[.]yolasite[.]com |
[1] Phishing sites are typically served on a specific URL and not on the root, e.g., hxxp://example.com/login.html rather than hxxp://example.com/. Full URLs are not provided here.
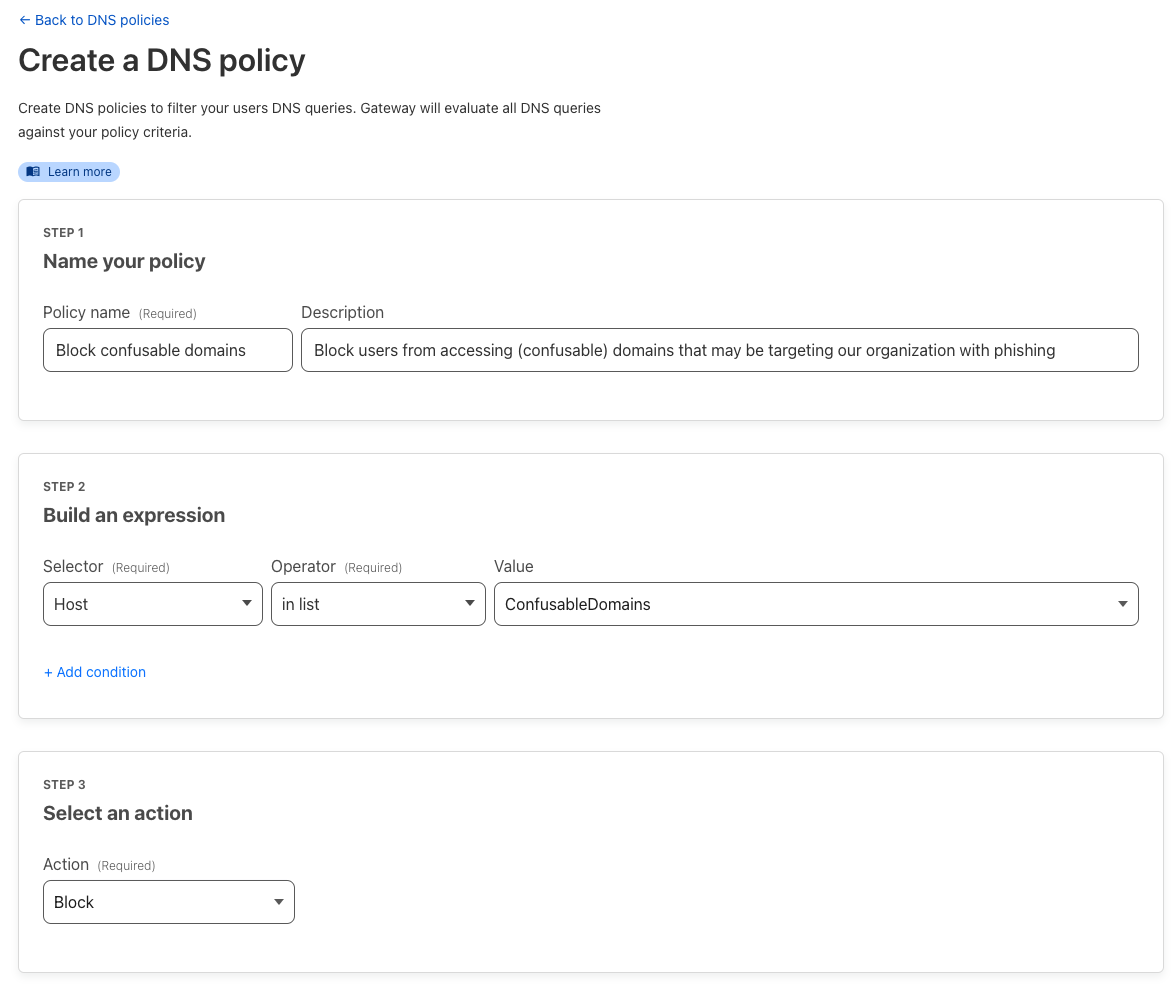
Combining threat intelligence capabilities with Zero Trust enforcement
The new features become a lot more effective for customers using our Zero Trust product suite. You can in fact easily block any confusable domains found as soon as they are detected by creating Cloudflare Gateway or DNS policy rules. This immediately stops your users from resolving or browsing to potentially malicious sites thwarting attacks before they happen.
Future enhancements
The new features are just the start of our broader brand infringement and anti-phishing security portfolio.
Matching against SSL/TLS certificates
In addition to matching against domains, we plan to also match against new SSL/TLS certificates logged to Nimbus, our Certificate Transparency log. By analyzing CT logs, we can identify potentially fraudulent certificates that may be used in phishing attacks. This is helpful as certificates are typically created shortly after domain registration in an attempt to give the phishing site more legitimacy by supporting HTTPS.
Automatic population of managed lists
While today customers can script updates to custom lists referenced in a Zero Trust blocking rule, as mentioned above, we plan to automatically add domains to dynamically updating lists. Additionally, we will automatically add matching domains to lists that can be used in Zero Trust rules, e.g. blocking from Gateway.
Changes in domain ownership and other metadata
Lastly, we plan to provide the ability to monitor domains for changes in ownership or other metadata, such as registrant, name servers, or resolved IP addresses. This would enable customers to track changes in key information related to their domains and take appropriate action if necessary.
Getting started
If you’re an Enterprise customer, sign up for Beta access for Brand protection now to gain access to private scanning for your domains, save queries and set up alerts on matched domains.


