Website Malware Removal: Phishing
As we continue on our Malware Removal series we turn our attention to the increasing threat of Phishing infections.
Just like a fisherman casts and reels with his fishing rod, a “phisher-man” will try their luck baiting users with fake pages, often in the form of login pages. These copied website pages are cast into infected websites with the hope that some users will bite, and get reeled into giving away their secret data. Wielding the web development and scripting knowledge necessary to make forms that look convincingly realistic, hackers lure unsuspecting users into entering their credentials on the imitated page.
These infections are known as Phishing Lures.
Any website, regardless of platform, can be prey to phishing infections. Unlike other tactics that look to abuse audiences or take advantage of popularity, think Blackhat SEO infections, this one focuses on your web server resources. This type of infection leverages the compromised website as the housing shell and delivery mechanism.
This delivery mechanism is used to serve pages and scripts built to social-engineer users into thinking they are official providers, often in the form of emails.
Because of it’s design, the attackers are able to abuse the users trust.
Phishing attacks can be devastating to the compromised website. Due to a damaged reputation, the website can suffer drops in search engine rankings, along with the brand distrust that comes from harboring pages that steal private user information.
Many Lakes and Many Places to Phish
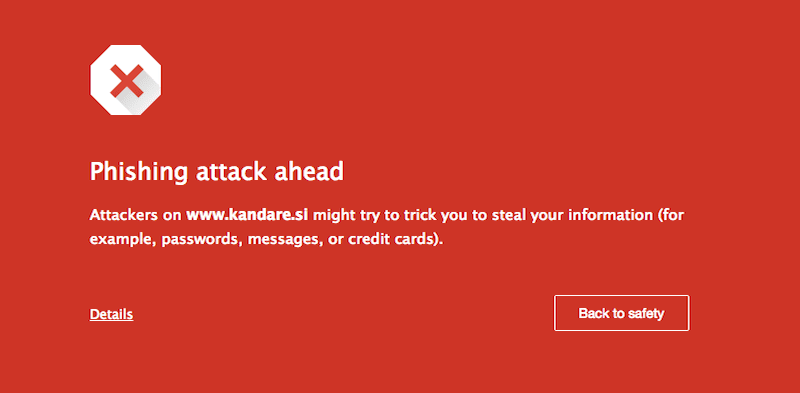
Do not be fooled into thinking some websites are immune to a phishing infection. Phishing is a conceptual task centered around taking advantage of the users trust. The attacker could be intent in distributing malware, stealing private / secret data, or any number of nefarious acts. They do it using deception and illusion; it is not bound to a specific technology, framework or CMS to make it work. The infection makes its way into files where it is able to deliver very official looking content to unsuspecting victims. If the user does not pay attention to the actual location of the URL or the SSL certificate, looking only at the webpage itself, then a password to an important social network, email portal or bank account could be exposed to a malicious attacker.
We have tracked numerous instances of phishing activity on websites that we protect, and have even documented examples of phishing in the wild. The following screenshot demonstrates where a phishing page had been hidden inside a Joomla website:
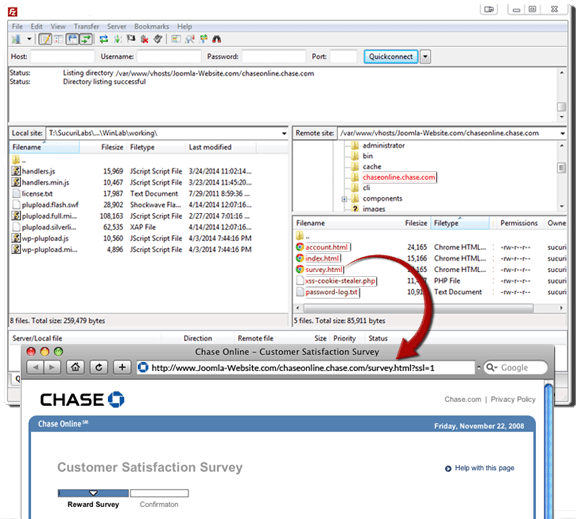
Infected Joomla website, phishing with fake Chase Bank page
It did not do much to disguise itself, as it was simple to exploit an unpatched vulnerability in the Joomla website. It then created a new directory in the root of the website where the fake Chase Bank pages could be hosted.
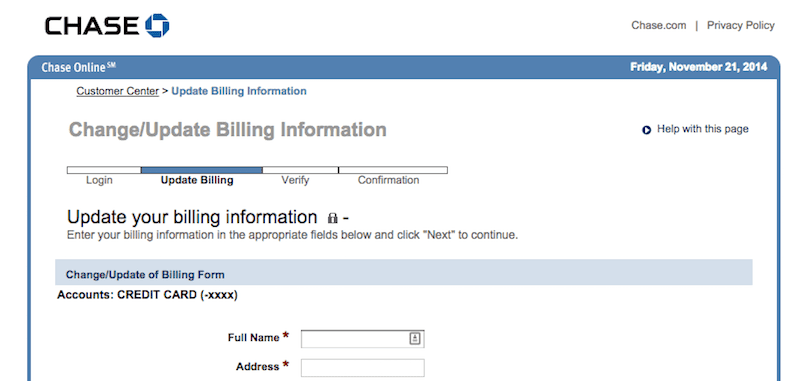
These pages coerce the user into giving away personally identifiable information (PII) as part of a “customer satisfaction survey” that offers a chance to receive a cash prize as incentive for filling it out. In actuality, the personal information and credentials are being captured by way of having all details of POST requests logged in a nearby file. This means anything submitted through the phishing form will be recorded by the hacker. As an added bonus, the infection also attempts to hook into the victim browser and steal any active cookies for use in accessing other accounts as well.
Looking back at another post written about Phishing on Magento Sites, it can be seen that the same style of attacks can apply to multiple ecosystems. Utilizing the ins and outs of HTML, ASP, PHP and JavaScript, a phishing file can live in any kind of environment that a webserver can provide, this is true for all website regardless of platform and technology.
WordPress is no stranger to Phishing attacks, similar to the examples above with Magento and Joomla, there are various cases that show how WordPress websites are being abused with Phishing infections.
Using Better Bait and Tackle

QR Code Phishing
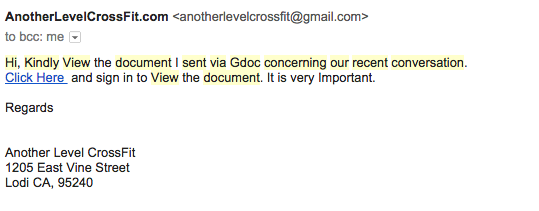
What makes this difficult to detect as an attack is all the additional layers of illusion that prevent victims from seeing that they are not actually getting to where they want to go. Once these pages are generated and placed onto a host website, they are ready for distribution to unknowing users. It is not prudent to simply ask them to do their banking at NotABankingSite.com/new-folder/bank-account-page.php. However, it gets trickier when link-shortening services are used, or carefully crafted subdomain/domain name combos are made to look like real addresses, as in the following examples: facebo.co.uk, or account-1.chase.com.on-linebanking.com, or simlt bit.ly/11jeGil. Going a step further, information thieves can weave these links into emails to resemble real messages from official companies, making them even harder to spot. An attacker can even make custom QR codes to entice users to access a link without ever displaying the text of the URL to the phishing page.
Removing Phishing Malware
When we talk about removing, we have to understand that the issue with Phishing is not removing, but detection. Unlike other attack methods that depend on browser events to occur, Phishing lures sit idle until employed by the attacker (i.e., used in email, sms, social media, etc.. campaigns).
Phishing pages in it of themselves often don’t have malware injected in them, so they don’t attempt at doing anything malicious to the users machine or browsers. Instead, they depend on the users naiveness to capture their information once they freely give it up.
Unlike, other infection types, Phishing pages are also not injected in existing code bases, or linked to the site itself. This thwarts most of that the tools that search through websites, following links to pages in the sitemap and checking source code for malicious injections.
With that in mind, when we talk about removal, we have to first focus on detecting the infection. Here are some of our recommendations:
- Know your website, it’s site structure and what belongs.
- Employ tools that allow you to see when things change.
- Monitor all changes to core installation directories.
More often than note, attacker really love to inject their Phishing payloads inside the core directories of a website (most applicable to those that leverage a CMS). This means they are leveraging directories like /includes and /administrator in Joomla! and /wp-admin and /wp-includes in WordPress. Along with a number of others. Because of it’s nature however it’s impossible to guess where exactly it will be.
Because of these challenges, we recommend always replacing the core files of your website, if possible. Note however that it is not a matter of reinstalling the files, you must physically delete the core directories and install fresh a new copy. The reason for this is that when you reinstall via most CMS platforms they will only update existing files, they don’t remove all files and start fresh. If you recall our conversation above, Phishing infections are often stand alone files that sit idly waiting to be leveraged.
Another great remediation option is to regularly run an integrity check on all directories and files. You are checking to see if new files are added to directories, while also looking to see if files change (e.g., content changes, time stamp changes, access times). A script meant to compare the contents of an infected server to that of a clean server would reveal the discrepancy in lines of code and lists of files among the core assets of any CMS or website framework.
If a WordPress website is in use, site owners can take advantage of the Free WordPress Sucuri Security plugin, available int he WordPress repository. For those managing their own servers, we’d recommend looking at a Host Intrusion Detection System (HIDS) solution, something like OSSEC.
When it comes to Phishing, unfortunately, there is no simple answer at the moment, and while it’s not a Do It Yourself (DIY) type project, there are things you can do as outlined above. Your best defense is either employing professionals to help, or taking a more proactive posture to your security.
Website owners should perform regular audits, and constantly monitor the code and files that reside on their server, making it easy to spot phishing pages that are out of place.



No comments yet.